Using the Insights Dashboard
The Insights page provides a preview of a dashboard feature that provides a management view over all enterprise devices, with a sample page view.
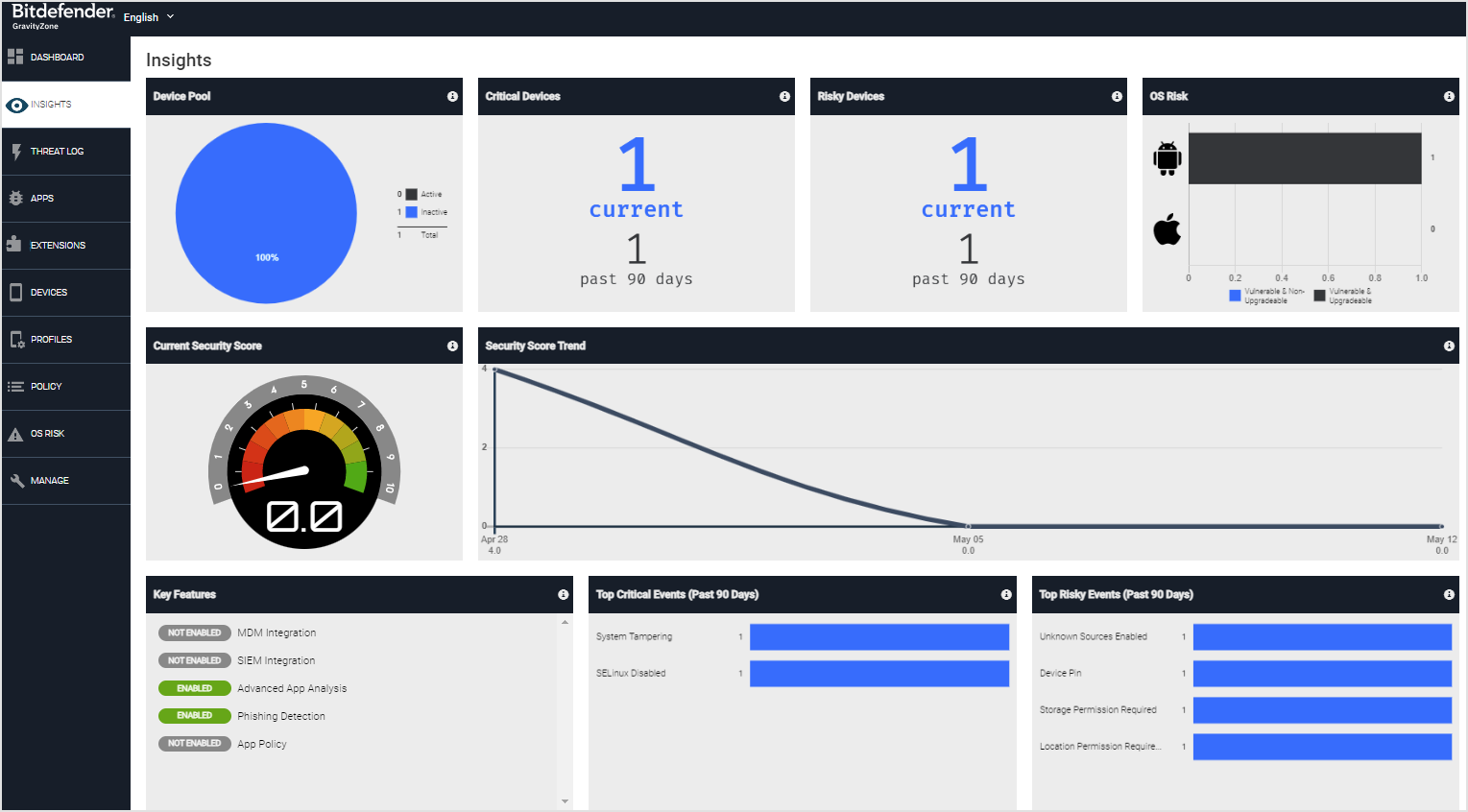
Device Pool - The pie graph shows the distribution of devices with the app activated and protected, with pending activation statuses.
Critical Devices - The number of devices with one or more critical threats over the last 90 days is shown.
Risky Devices - The number of devices with one or more risky events over the last 90 days is shown.
OS Risk - Android and iOS devices are vulnerable due to outdated and vulnerable operating system versions, and must be updated to remove this risk.
Current Security Score - The current security score across all devices is based on an assessment of the Mobile Security app activation, risks, and threats. It increases as the activation of the app increases and as device risks and threats decrease.
Note
The security score calculation is based on Device Pool, Critical Devices, Risky Devices, and OS Risk data. It does not include the number of devices that had critical threats and risky events over the last 90 days. This score is calculated using data from the previous day.
Security Score Trend - A security score graph can be displayed over a daily, weekly, or monthly time frame.
Key Features - The enabled or disabled status values for key features of the solution, such as MDM Integration and Advanced App Analysis.
Top Critical Events - The top five critical threats are sorted based on the number of events occurring over the last 90 days.
Top Risky Events - The top five risky events are sorted based on the number of events occurring over the last 90 days.
The critical threats shown in the Insights Dashboard
This section provides information on the threats and their meanings. These threats display for the threat policy, where system administrators can set severity levels.
Mitigating a threat is making the threat less of a risk or removing the risk altogether. Each threat indicates if it has automatic or manual mitigation.
Automatic - changes to the device or other risk factors can change, and the threat can be automatically mitigated through the Mobile security console or app. The status of the threat then changes from a Pending state to a Fixed state.
Manual - an administrator must mark the threat as fixed or approved.
Item | Threat description | Default Severity | Mobile Security for Android | Mobile Security for iOS | Mobile Security for Chrome OS | Security for Chrome | Internal threat name, ID | Mitigation | Vector | Tag | Mitre tactics |
|---|---|---|---|---|---|---|---|---|---|---|---|
App Pending Activation | App activation for the Mobile Threat Defense (MTD) application is not complete. Notification email: Indicates that the server detects the threat and sends a notification (email) without a device alert display within the application. | Low | Yes | Yes | Yes | DEVICE_PENDING_ACTIVATION, 200 | Automatic | Device | host.device_pending_activation | n/a | |
Danger Zone Connected | The device connected to a Wi-Fi network where malicious attacks have been observed. | Low | Yes | Yes | Yes | DANGERZONE_CONNECTED, 79 | Automatic | Network | network.danger_zone_connected | Initial Access, Network Effects | |
Danger Zone Nearby | The device is near a Wi-Fi network where malicious attacks have been observed. | Normal | Yes | Yes | Yes | DANGERZONE_NEARBY, 80 | Automatic | Network | network.danger_zone_nearby | Initial Access, Network Effects | |
Detection Inactive | Mobile threat detection is inactive. No method of detection is active, either from the app or VPN. | Elevated | Yes | Yes | Yes | DETECTION_INACTIVE, 1007 | Automatic | Device | host.detection_inactive | n/a | |
Detection Pending Activation | MTD detection is pending activation. | Low | Yes | Yes | Yes | DETECTION_PENDING_ACTIVATION, 1006 | Automatic | Device | host.detection_pending_activation | n/a | |
Device Compromised via Phishing Attack | The device was compromised by a sophisticated kill chain attack that started with a phishing threat and ended leaving the device compromised. Type is composite. [f] | Critical | Yes | Yes | Yes | DEVICE_COMPROMISED_VIA_PHISHING_ATTACK, 123 | Manual | Network | pattern.device_compromised_via_phishing_attack | Initial Access, Execution, Persistence, Privilege Escalation, Credential Access, Impact, Network Effects | |
High Risk Browser Extension | A Chrome extension is detected that has one or more privacy and/or security concerns that may put your personal and confidential information at risk. | Elevated | Yes | Automatic | App | chromeos.extension.high_risk | Persistence, Credential Access, Discovery, Collection, Execution | ||||
Inactive App | A certain amount of time has passed and the app has not communicated with the server. Notification email: [c] | Elevated | Yes | Yes | Yes | INACTIVE_APP, 100 | Automatic | Device | app.dormant | n/a | |
Link Verification Disabled - Safari Extension | Link verification using the Safari browser extension is disabled on the device. | Elevated | - | - | - | SAFARI_EXTENSION_DISABLED, 151 | Automatic | Network | network.safari_extension_disabled | n/a | |
MTD Is Not Activated on Both Work and Personal Profiles - Android Enterprise | The Mobile Threat Defense (MTD) application is not activated on both the personal and work profiles on this device. Install and activate the MTD app in both locations to ensure full device protection. | Elevated | Yes | - | - | ZIPS_NOT_RUNNING_ON_CONTAINER, 78 | Automatic | Device | host.afw_both_profiles_not_activated | n/a | |
Out of Compliance App | One or more apps are found on the device that are marked as Out-of- Compliance apps. | Elevated | Yes | Yes | Yes | OUT_OF_COMPLIANCE_APP, 93 | Automatic | App | host.app_out_of_compliance | Exfiltration, Collection, Impact | |
Out of Compliance Browser Extension | A Chrome extension is detected that is marked out of compliance with your organization's policies. It is recommended that you remove it from your Chrome browser. | Elevated | - | - | - | Yes | OOC_BROWSER_EXTENSION, 1003 | Automatic | App | chromeos.extension.ooc | Persistence, Credential Access, Discovery, Collection, Execution |
Phishing Protection - Link Tapped | A potentially malicious website address (URL) link was tapped on the device. | Elevated | Yes | Yes | Yes | Yes | MALICIOUS_WEBSITE, 9 | Automatic | Device | host.site-insight.link-tapped | Initial Access, Credential Access, Network Effects |
Phishing Protection - Link Visited | A user tapped a potentially malicious URL on the device. The user was warned of potential danger with the linked site and chose to continue to the website after the warning. | Elevated | Yes | Yes | Yes | Yes | MALICIOUS_WEBSITE_OPENED, 72 | Automatic | Device | host.site-insight.link-visited | Initial Access, Credential Access, Network Effects, Execution, Privilege Escalation |
Risky Site Blocked | A potentially malicious website address (URL) link was blocked on the device. [j] | Elevated | Yes | Yes | Yes | Yes | MAL_WEBSITE_BLOCKED, 137 | Automatic | Device | content_filter.malsite_blocked | Initial Access |
Risky Site - Link Tapped | A potentially malicious website address (URL) link was tapped on the device. [j] | Elevated | Yes | Yes | Yes | Yes | MAL_WEBSITE_TAPPED, 135 | Automatic | Device | content_filter.malsite_tapped | Initial Access |
Risky Site - Link Visited | A user tapped a potentially malicious link on the device. The user was warned of potential danger with the linked site and chose to continue to the website after the warning. [j] | Critical | Yes | Yes | Yes | Yes | MAL_WEBSITE_VISITED, 136 | Automatic | Device | content_filter.malsite_visited | Initial Access |
Sideloaded Browser Extension | A sideloaded extension is detected, which was not installed from an official web store. These extensions and their developers may not be verified and can present a security risk. | Elevated | - | - | - | Yes | SIDELOADED_BROWSER_EXTENSION, 1005 | Automatic | App | chromeos.extension.sideloaded | Persistence, Credential Access, Discovery, Collection, Execution |
Site Blocked | A user tapped on website content not approved by your organization and the site was blocked. [j] | Elevated | Yes | Yes | Yes | Yes | WEBSITE_BLOCKED, 134 | Automatic | Device | content_filter.blocked | Initial Access |
Site Warning - Link Tapped | Website content not approved by your organization was tapped on the device. [j] | Elevated | Yes | Yes | Yes | Yes | WEBSITE_TAPPED, 132 | Automatic | Device | content_filter.website_tapped | Initial Access |
Site Warning - Link Visited | A user tapped on website content not approved by your organization. The user was warned the website content does not comply with your organization's policies and chose to continue to the website after the warning. [j] | Elevated | Yes | Yes | Yes | Yes | WEBSITE_VISITED, 133 | Automatic | Device | content_filter.website_visited | Initial Access |
Suspicious Browser Extension | An unsafe extension is detected. It is strongly recommended that you remove the extension immediately. | Critical | - | - | - | Yes | SUSPICIOUS_BROWSER_EXTENSION, 1002 | Automatic | App | chromeos.extension.suspicious | Persistence, Credential Access, Discovery, Collection, Execution |
Suspicious iOS App | A known malicious app is detected and can attempt to take control of the device in some manner, such as elevation of privileges or spyware. | Critical | - | Yes | - | SUSPICIOUS_IPA, 42 | Automatic | App | host.ipa.malicious | Initial Access, Persistence, Exfiltration, Impact, Credential Access, Execution, Collection | |
Suspicious Profile | A suspicious profile is a new profile introduced into the environment and is not explicitly trusted or untrusted. An administrator must review the profile and mark the profile as trusted or untrusted. | Elevated | - | Yes | - | SUSPICIOUS_PROFILE, 45 | Automatic | Device | host.profile.suspicious | Initial Access, Persistence, Exfiltration, Impact, Credential Access, Execution, Collection | |
Untrusted Profile | An untrusted profile is a profile installed on one or more devices and is unsafe on your devices. An untrusted profile installed on devices can be used to control devices remotely, monitor and manipulate user activities, and hijack users' traffic. | Critical | - | Yes | - | UNTRUSTED_PROFILE, 24 | Automatic | Device | host.profile.untrusted | Initial Access, Persistence, Exfiltration, Impact, Credential Access, Execution, Collection |
Risky events in the Insights Dashboard
The events categorized as risky events in the Insights dashboard display are:
Note
A mobile threat defense platform can detect "risky events" such as malicious apps, network anomalies, device vulnerability exploitation, jailbreaking/rooting, phishing attacks, device compromise indicators, and unusual device activities.
These events can include malicious app installation, network anomalies, device vulnerability exploitation, jailbreaking/rooting attempts, phishing attacks, device compromise indicators, and abnormal device activities. These alerts help protect against potential security threats.
Android Debug Bridge (ADB) Apps Not Verified
Android Device - Compatibility Not Test By Google
BlueBorne Vulnerability
Daemon Anomaly
Developer Options
Device Encryption
Device Pin
Google Play Protect Disabled
MITM - Fake SSL certificate
Rogue Access Point: Nearby
Sideloaded App(s)
Site Insight - Link Tapped
Stagefright Vulnerability
Suspicious Profile
Unknown Sources Enabled
USB Debugging Mode
Mobile security app is not activated on both work and personal profiles - Android for Work
Key features
The key features section shows a summary of the enabled or disabled status values for key features of the solution. These features show status for:
MDM Integration - Enables the synchronization of devices, defines group usage in policy and configuration items, and provides granular protection mechanisms. This feature is enabled if there is at least one MDM integration set up in Mobile Security Console.
SIEM Integration - Provides a secure method for pulling security events from the mobile security console. This is enabled if there is at least one SIEM integration setup in the Manage > Integrations > Data Export section of Mobile Security Console or with the Syslog pull integration.
Advanced App Analysis - Assesses mobile app risk among company devices, enabling intelligent identification of safe and risky apps, and setting security policies to mitigate risk. This is enabled by default for the enterprise under normal circumstances.
Phishing Detection - Enables administrators to warn and protect users from accessing harmful websites and links that may pose a danger. This is enabled in the key features of URL sharing or VPN-based phishing is enabled for at least one group within Mobile Security Console.
App Policy - Enables the application vetting capability. This feature is enabled if at least one app policy has been created under the Policy page.