Custom detection rules
Use the Custom detection rules page to define rules that mark specific behavior from your environment as a valid detection, and generate corresponding incidents in The Incidents page.
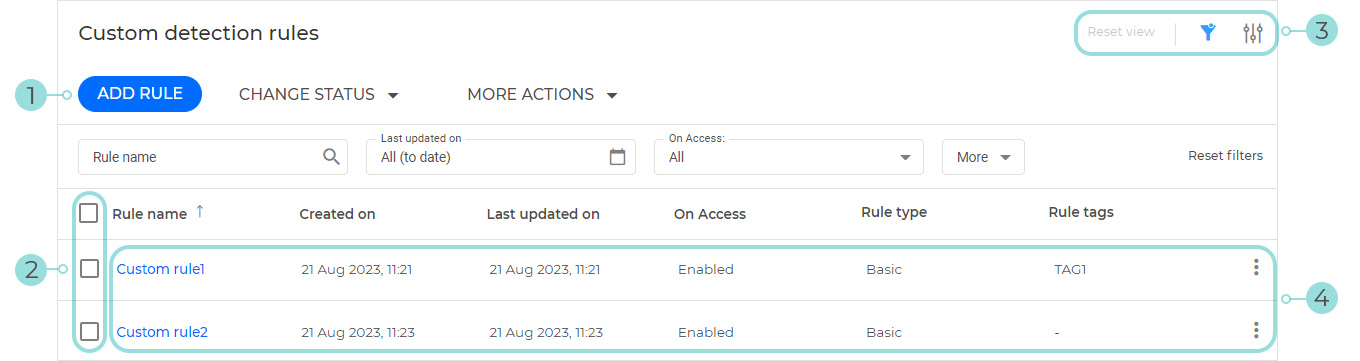
Click the Add rule button to create a new custom detection rule. For more details, refer to Creating Custom detection rules.
Select the global check box or the individual rule check boxes to select them. After selecting one or more rules, you can manage them in the following ways:
To enable or disable the rules, click the Change status drop-down menu and choose the desired action.
To delete the rules, click the More actions drop-down menu and select Delete.
Use these action buttons to customize your grid:
Click the Reset view button to reset the grid to the default settings in terms of displayed columns and filters. This option also clears existing filters and their values.
Click the
 Show or hide filters button to show or hide the filters bar.
Show or hide filters button to show or hide the filters bar.Click the
 Open Settings button to add or remove columns from the grid.
Open Settings button to add or remove columns from the grid.
Click a rule's name to enter edit mode and update the rule. Click a rule in the list to expand its Details panel, view the rule details, update it or delete it. For more details, refer to Detection rule Details panel.
Creating Custom detection rules
To create custom detection rules, follow these steps:
In the Custom detection rules page, click the Add rule button.
You will be redirected to the Add rule page.

Note
If you are enrolled in the YARA detection rules Early Access program, you have the option to switch to the YARA rule definition page.
In the Detection rule definition section, select the type of element you want to include in the detection rule.

The element types are:
Process
File
Connection
Registry
Select the matching criteria:

Select one of the available criteria options.
Select the type of relationship between the matching criteria and its value:
Is - matches the exact value entered in the value field.
Contains - matches all values that contain the string entered in the value field (for example, file extensions).
Important
Use wildcards with caution when creating a detection rule, as it raises the risk of making it too generic. Generic rules may cause an overflow of false-positive incidents.
Is one of - matches any of the values entered in the value field (an
ORoperation is performed between the values). You must press Enter after each value, to complete the action.
Enter the specific value for each criteria.
Use the Add new button to add new criteria to the rule.
Note
The rule triggers incidents only when all criteria is met (an
ANDoperation is performed between the added criteria).In the Rule configuration section, add a rule name, a rule description, and rule-related tags.
Rule tags can help you identify, group, and sort for rules as needed. If you do not have a tag that suits your rule, you can click the Create tag button, and add one.

To activate the rule immediately after creation, select the On-access scanning checkbox.
Enabling this option generates alerts whenever the pattern listed in the rule is detected on an endpoint.
You can view the alerts in the Incidents > Search page by using the
other.rule_idfield in your query.In the Rule outcome section, set the severity of the alerts triggered by this rule.
Optionally, you can select the Generate security incident checkbox.
Click Next.
In the Rule targets window, select which endpoints the rule will scan. You can select the entire company or specific endpoint tags. These tags are created and managed in Network > Tags Management.
When you select the Endpoint tags option, you can choose the tags from the list in the left-side menu, and your current selection of tags will appear in the right-side menu.
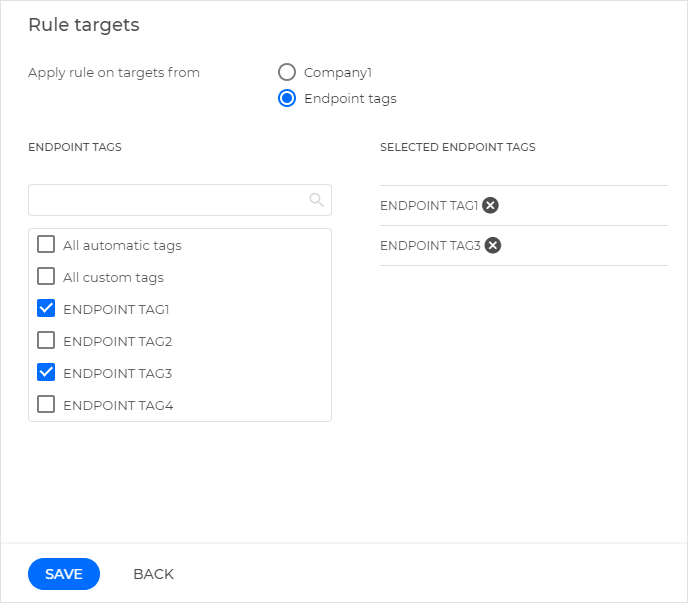
Click Save.
The new rule is now available in the Custom detection rules grid.
Detection rule Details panel
The rule Details panel contains information on the selected rule, rule criteria, rule tags, rule outcome, and options to update it or delete it.
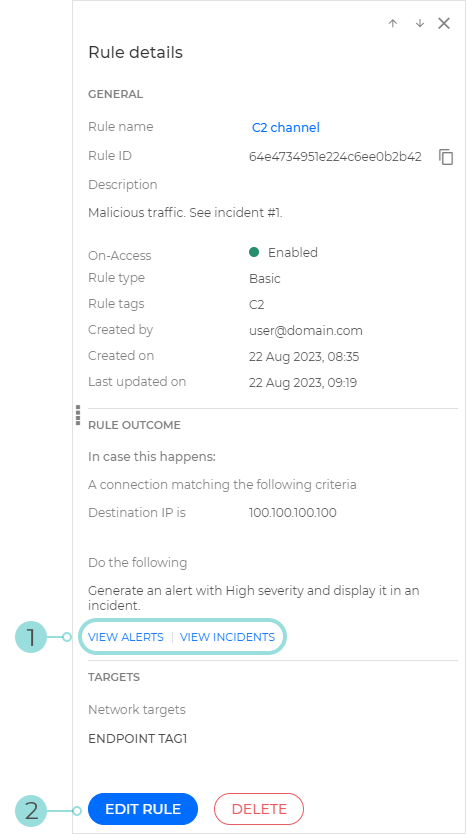
The View alerts and View incidents options redirect you to the Search and the Incidents section, respectively. Prefilled queries run automatically to retrieve all the alerts or incidents triggered by the rule.
The Edit rule button brings up the rule definition window, where you can change the rule settings.