Onboarding a Google Cloud Platform (GCP) Organization
Cloud accounts in the Google Cloud Platform (GCP) are referred to as projects. They can be grouped together in entities called organizations.
You can integrate a single cloud account (or a project), or a group of accounts (an organization).
Prerequisites:
A GCP account within the organization assigned with the Organization Administrator and Organization Role Administrator roles.
An active Cloud Billing Account
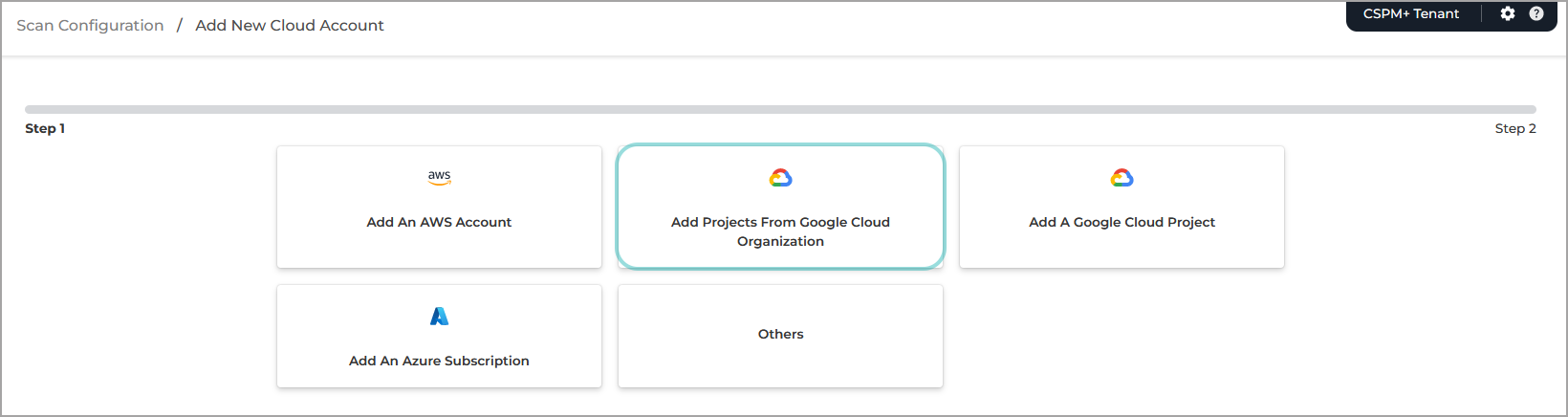
Add a GCP Cloud Organization
Under Scan Configuration, select Add projects from a Google Cloud Organization.
Open a new browser tab or window and login to the GCP console.
Create a new project within the organization to ensure API limits for GravityZone Cloud Security are controlled separately from production workloads:
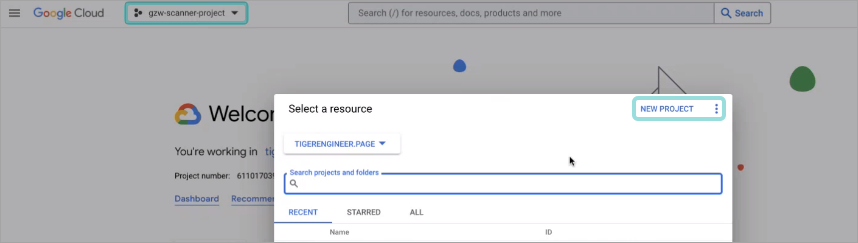
Click the Select Project button on the upper left side of the page.
The Select a project window is displayed.
Click New project
Enter a unique project name and click Create.
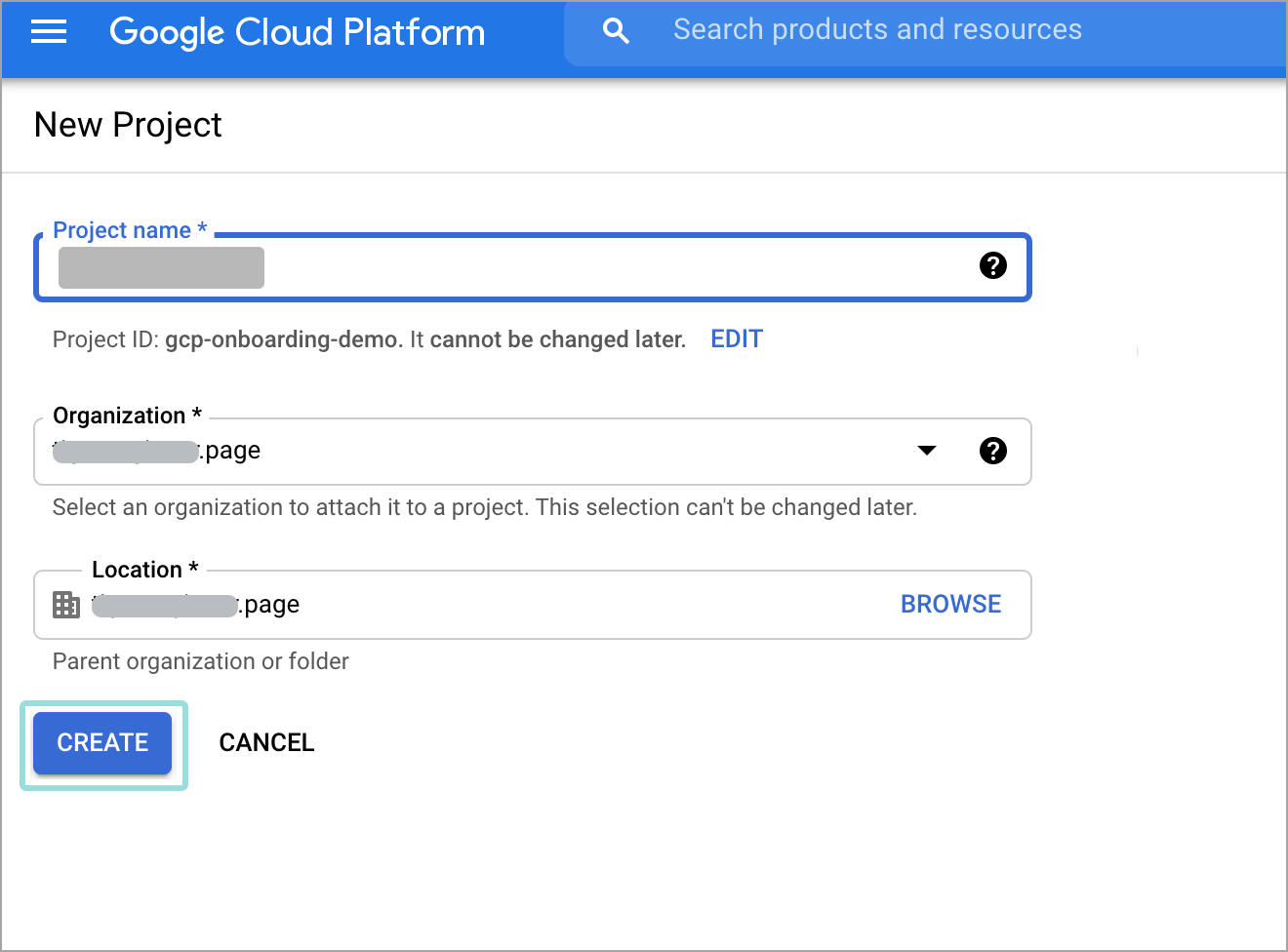
You will be redirected to the project view.
Click the menu button on the top left corner and select Billing.
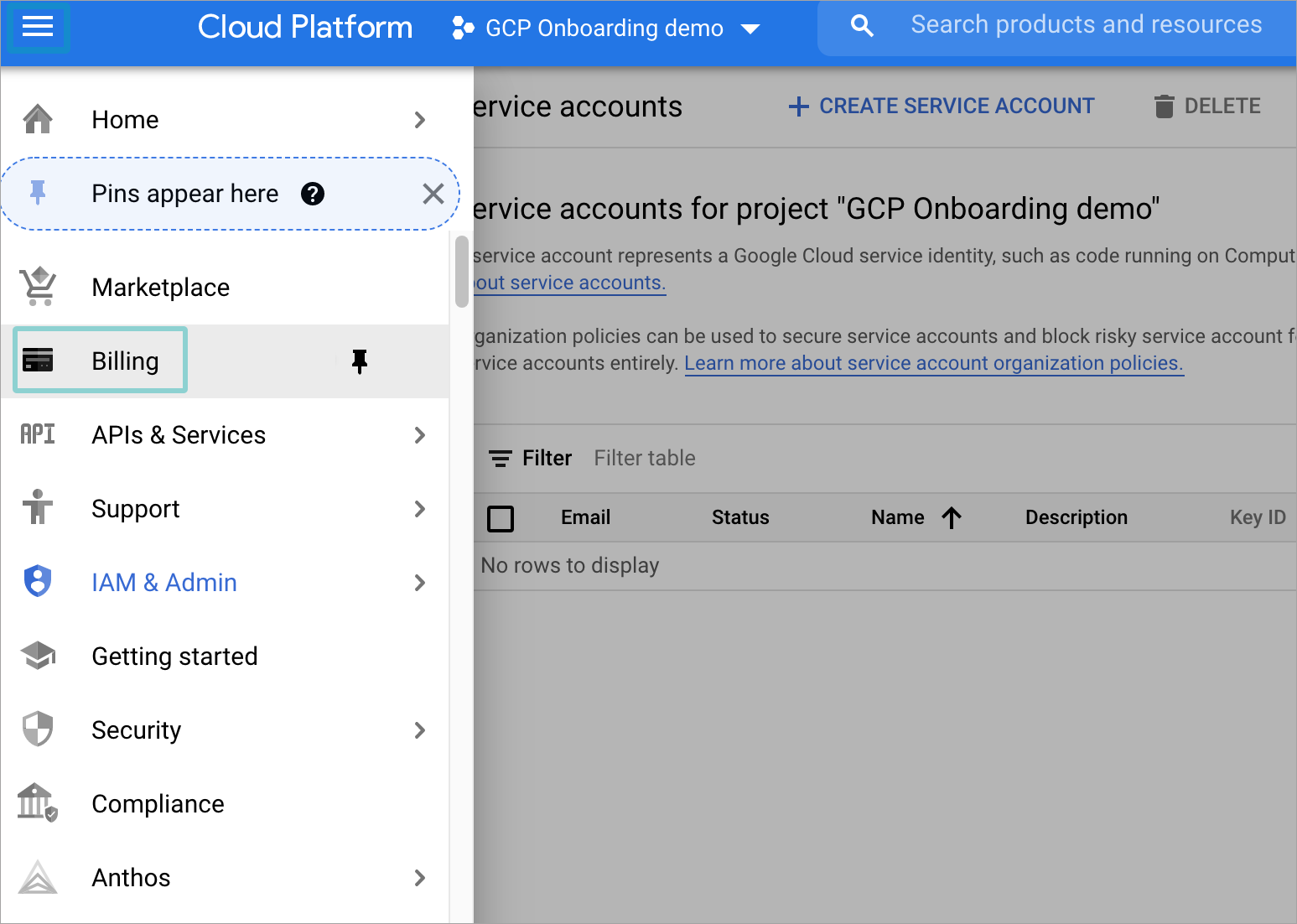
If a billing account has already been linked to the project, you should see the Billing Overview page.
If that is not the case, follow these steps:
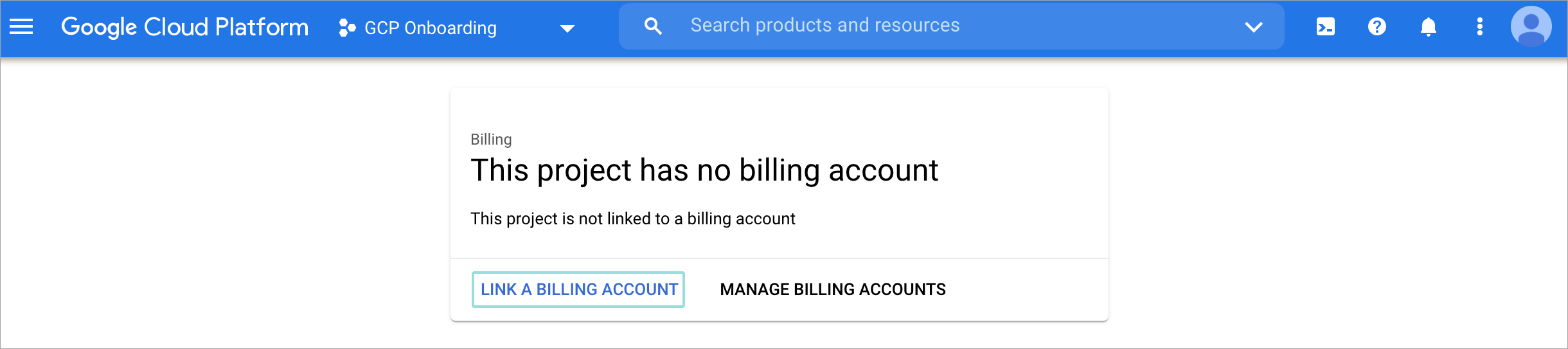
Click Link a billing account.
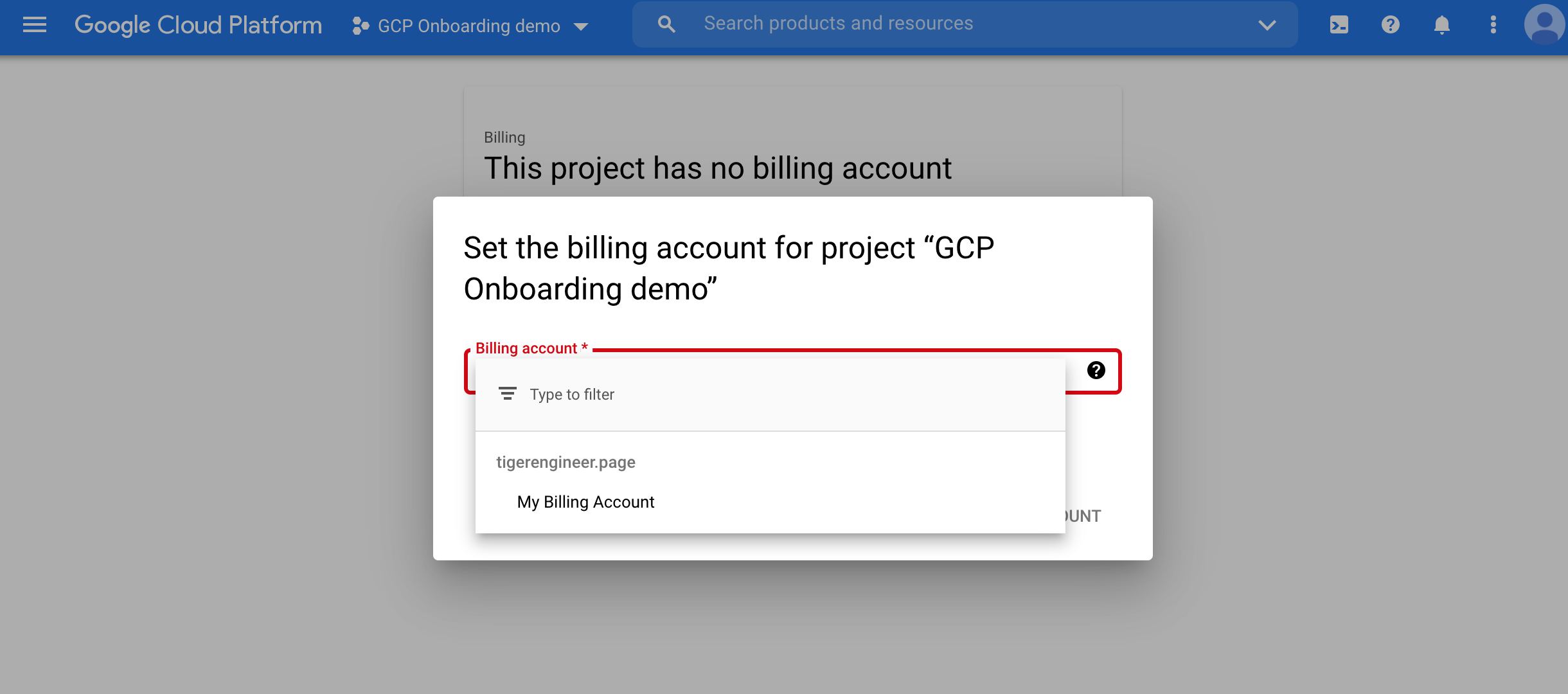
Select the billing account you would like to associate the project with from the dropdown menu and click on Set Account.
Go to the IAM & Admin page.
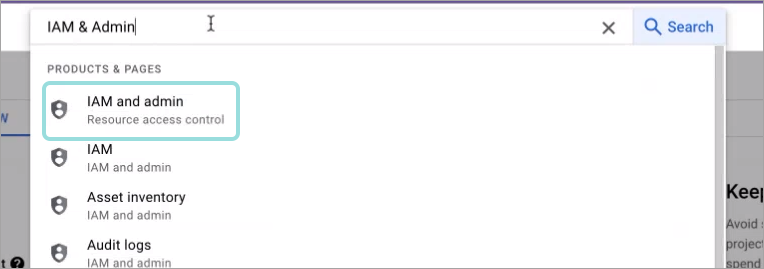
Select Service Accounts from the menu on the right side of the page.
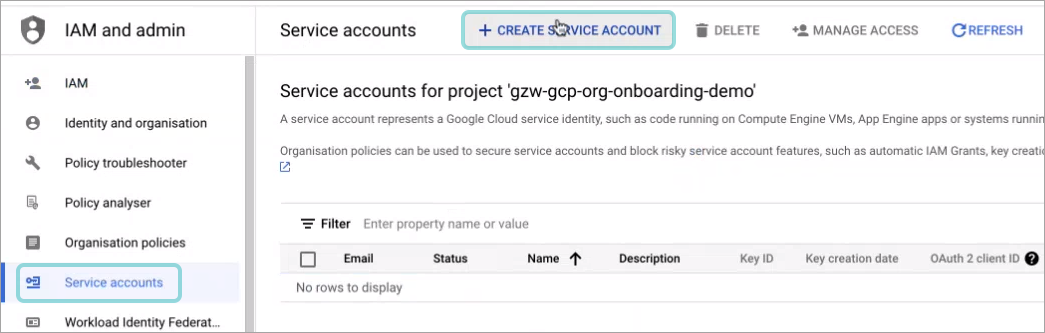
The Service accounts page is displayed.
Click + Create Service Account:
The Create service account window is displayed.
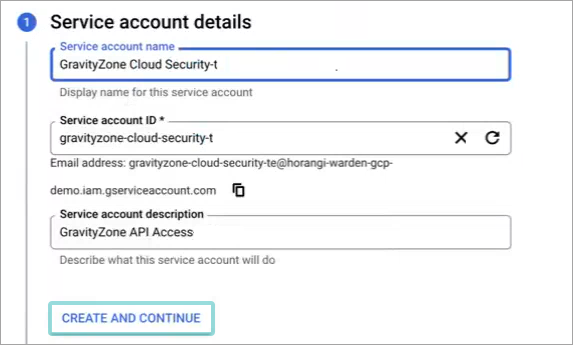
Fill in the information for the new account:
Under Service account name type in a descriptive name, such as
GravityZone Cloud Security(Optional) Edit the Service account ID. This is automatically generated based on the account name you previously entered.
Type in a clear description for the service account under Service account description, such as
GravityZone API Access.
Click Create and continue.
The Grant this service account access to project section is expanded.
Click Done.
The Service accounts page is displayed.
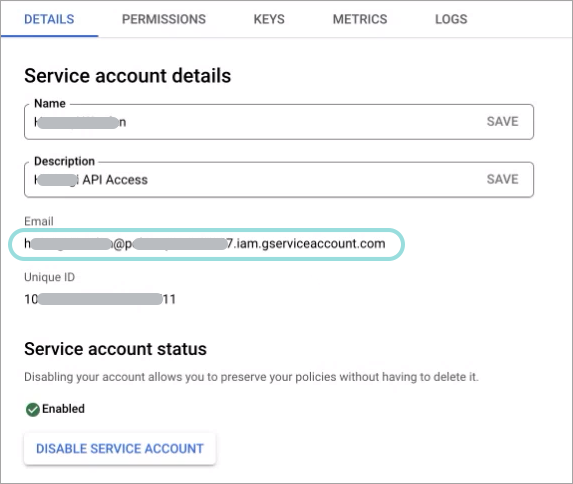
Write down the email address of the service account you just created in an accessible location:
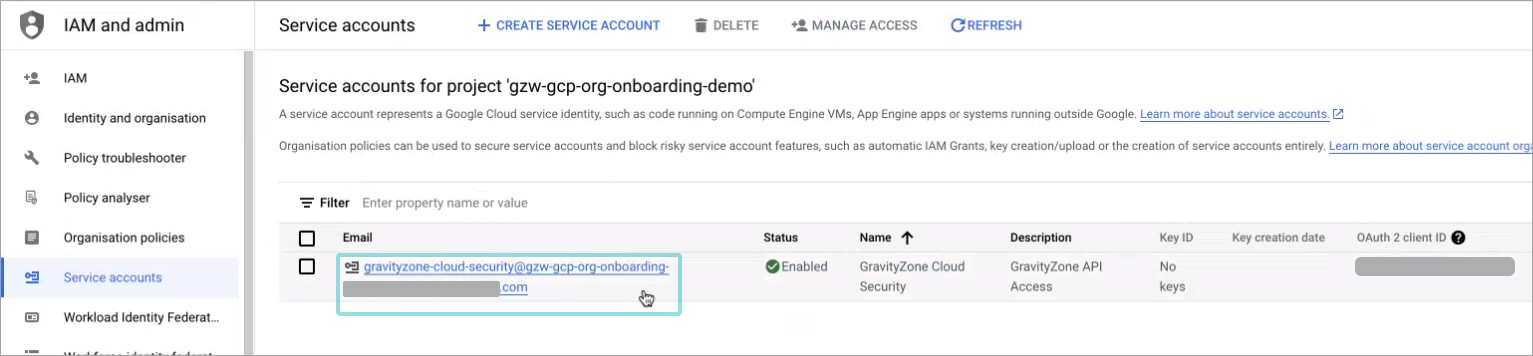
Click the address under the Email column.
The Service account details page is displayed.
Go to the Keys tab.
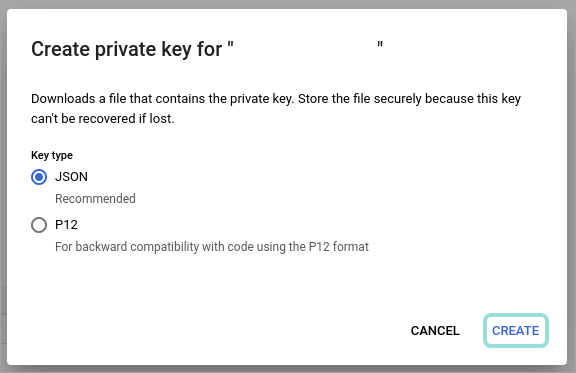
Click the Add key button and select Create new key:

Under Key type, make sure JSON is selected and click Create.
A
.JSONfile is downloaded to your computer.Enable the APIs necessary for Enable the APIs necessary for Warden to work. to work:
The Compute Engine and Cloud DNS APIs require you to have billing enabled on the projects you are onboarding.
Click the Select Project button on the upper left side of the page.
The Select a resource window is displayed.
Go to the All tab and select your organization.
Note
Organizations are marked with the
 icon.
icon.Click the Roles from the menu on the right side of the page.
The Roles page is displayed.
Click + Create role.
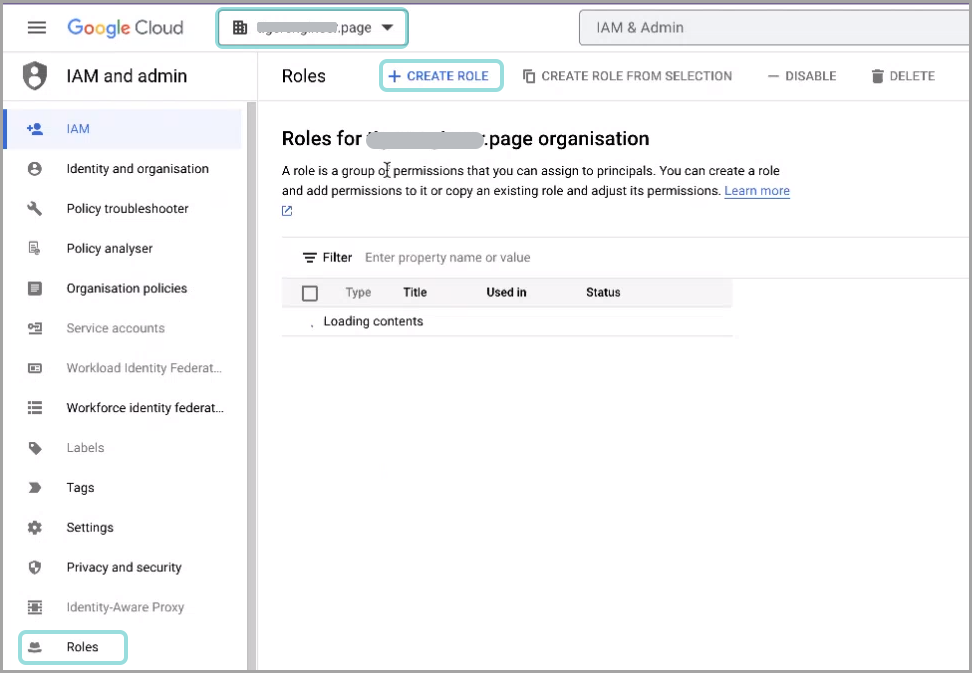
Fill in the role information:
Under Title, type in a descriptive name, such as
GravityZone Cloud Scanner.(optional) Edit the Description field to make the role more easily identifiable.
Under ID, type in an easily identifiable string, such as
GravityZoneCloudScanner.Note
This ID is unique per organization.
Click Add permissions:
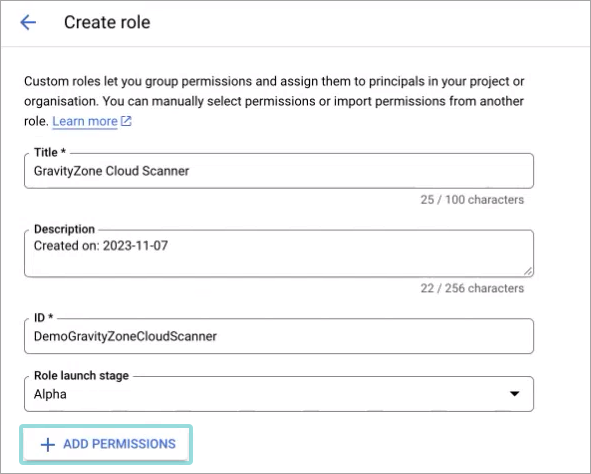
The Add permissions window is displayed.
Click the Filter field to search for the roles:
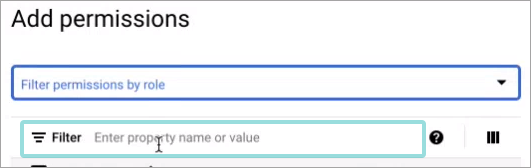
Type in the permission name.
Check the box next to the search result to select the permission:
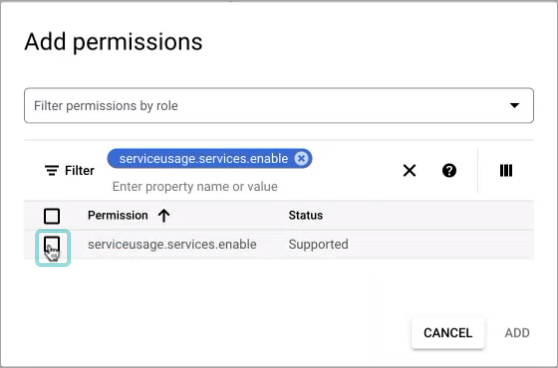
Perform steps 23 - 25 for each of these permissions:
serviceusage.services.enableserviceusage.services.getserviceusage.services.listcompute.projects.get
Click Add.
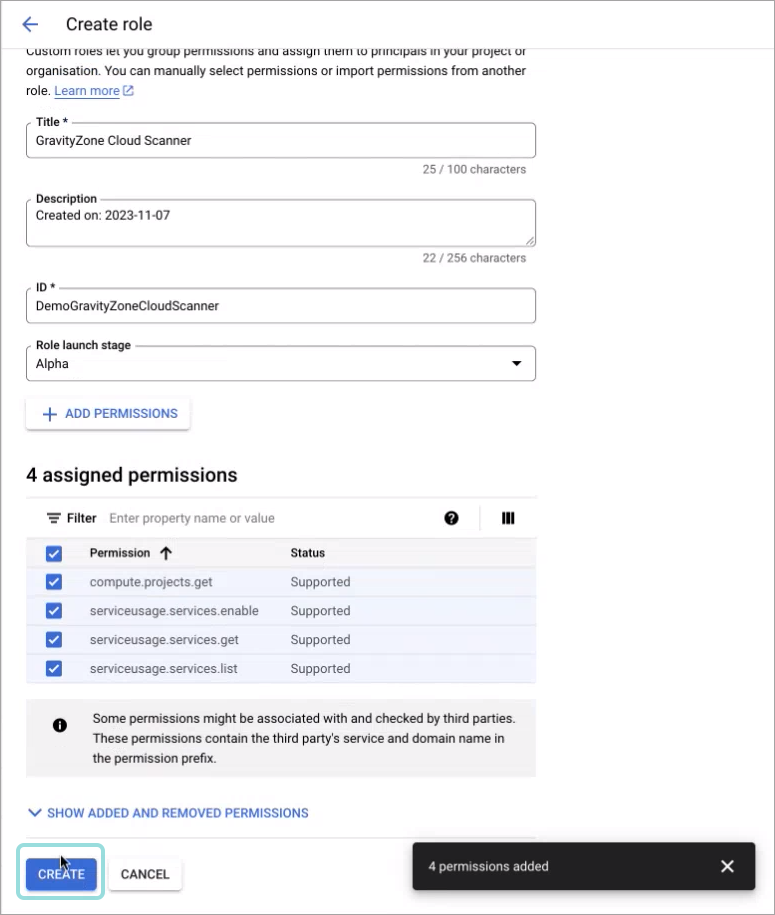
The permissions are displayed under the Create role window
Click Create:
Go to the IAM page.
Tip
Make sure your organization still appears in the selector on the upper left side of the page.
Click Grant access.
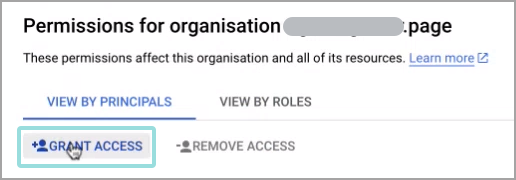
The Grant access page is displayed.
Paste the email address from Step 11 under the Add principals section.
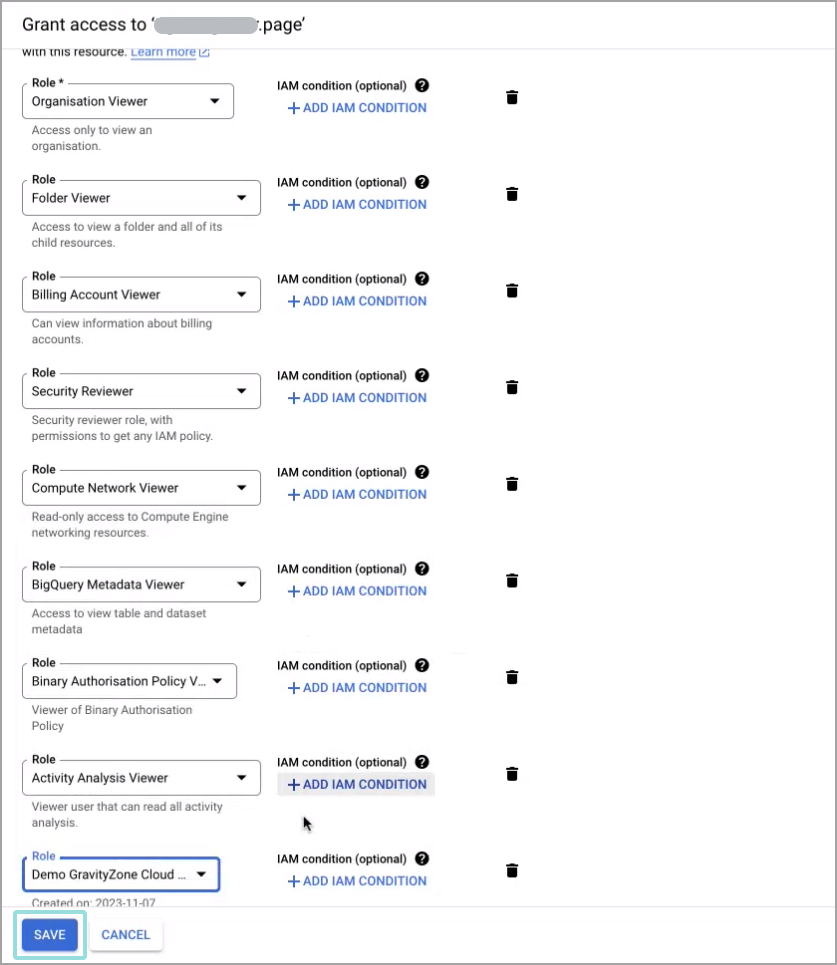
Click Select a role. Select each of the following roles:
Resource Manager > Organization Viewer
Resource Manager > Folder Viewer
Billing > Billing Account Viewer
IAM > Security Reviewer
Compute Engine > Compute Network Viewer
BigQuery > BigQuery Metadata Viewer
Binary Authorization > Binary Authorization Policy Viewer
Other > Activity Analysis Viewer
Custom > GravityZone Cloud Scanner (This is the Role created earlier)
Tip
If this role is not immediately available, wait for a few minutes for it to appear in the list.
Click Save.
Go back to the Scan Configuration browser page.
Copy and paste the contents of the JSON file into the API Credentials field.
Under the Identifier field type in
organizations/followed by organization ID, as it appears in your GCP console.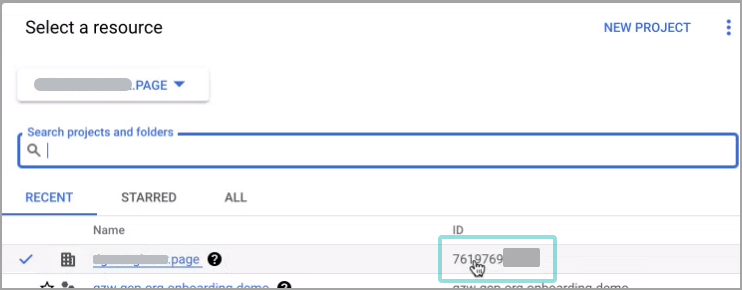
Under Google Cloud Organization Name paste the email address you copied at step 11.
Click Add.
Asset inventory onboarding
Enabling GravityZone Cloud Security to scan Google Workspace Identities provides you a more accurate representation of your cloud environment, by providing access to identity related metadata.
Tip
Once enabled, the benefits will apply to the information available in the Identities page, along with the Identities with access tab in the Resource Details panel from the Resources page.
To enable the workspace, you need admin permissions on the workspace account.
Enable GravityZone Cloud Security to scan Google Workspace Identities for a new Google Cloud Platform (GCP) account
To enable GravityZone Cloud Security to scan Google Workspace Identities for a new GCP account, follow the steps listed here and after that process is completed, continue with the below:
Open a new browser tab or window and log in to admin.google.com.
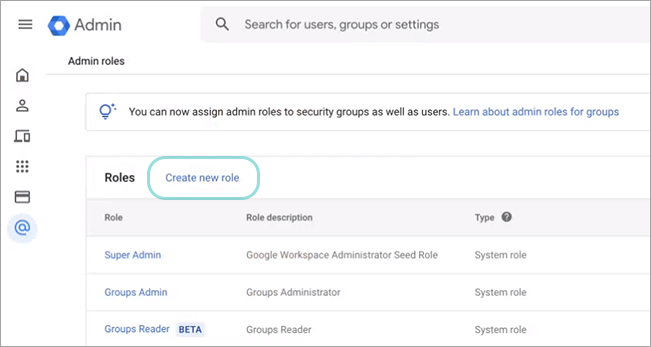
Navigate to Account > Admin Roles.
Click Create New Role.
Under Name, type in a descriptive name, such as
GravityZone Cloud Security.Click Continue.
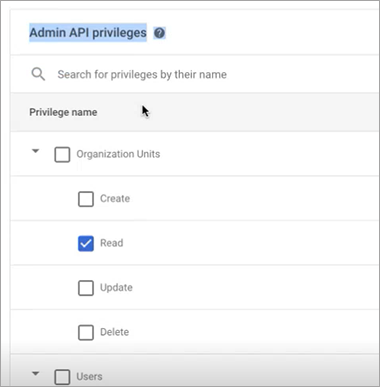
Scroll down to Admin API privileges, check the following checkboxes:
Users > Read
Groups > Read
Click Continue.
You will see 2 privileges selected.
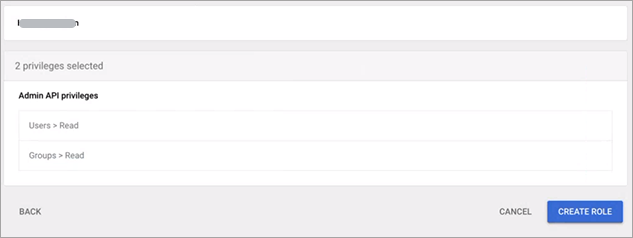
Click Create role.
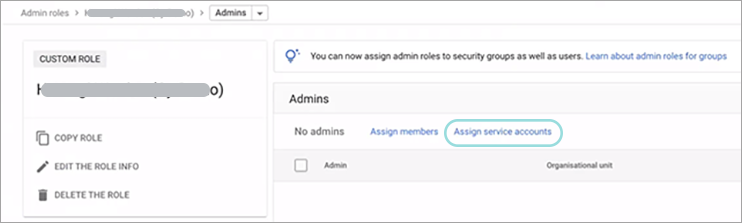
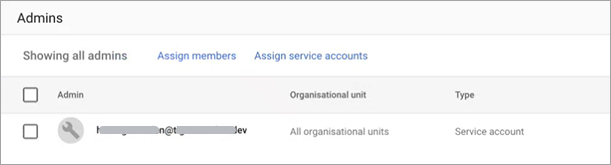
Click Assign service accounts.
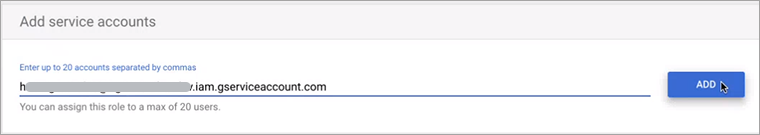
Enter the email of the previously created account.
Click Add.
Click Assign Role.
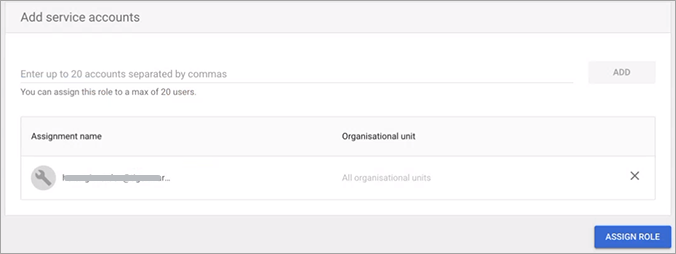
The role is added with the permissions selected previously.
Navigate to Settings > Integrations, select GCP Cloud Organization and click the Modify button to access the Google Cloud Organization card. From here, click Update and this will display a new information card with the API Credentials.
Note
Once the Asset Inventory is enabled, it also applies to all other projects and organizations inside the same Google workplace.
If you have an additional workspace, you need to enable this option again for one of its Projects or Organizations.
Enable GravityZone Cloud Security to scan Google Workspace Identities for an existing Google Cloud Platform (GCP) account
To enable GravityZone Cloud Security to scan Google Workspace Identities for an existing GCP account, you need to follow the exact same steps as for a new account. The only difference is that you need to obtain the email of the previously created account.
To find the email of the previously created account, refer to the steps bellow:
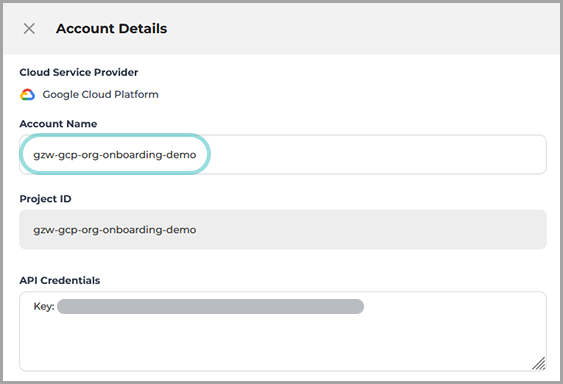
Navigate to Scan Configuration page, select the account and click the Edit icon.
From the Account Details panel, copy the Account Name details.
Open a new browser tab or window and log in to your Google Cloud Console.
Navigate to IAM & Admin and click Search a project.
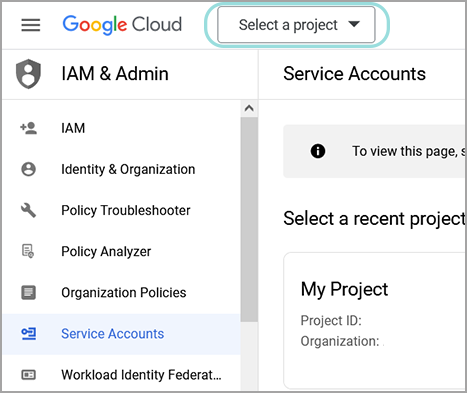
In the Search projects and folders field, type in or paste the info copied at step 2.
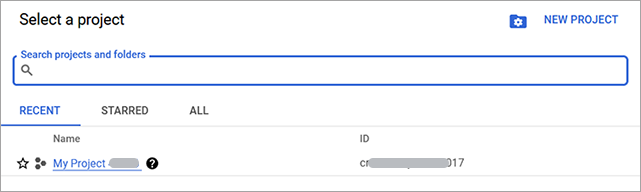
Once the project is selected, navigate to Service Accounts page and search for the API Credentials. You can copy the API Credentials from the Account Details panel (step 2).
Click the service account corresponding to the API Credentials.
From the Service account details page, you can then copy the email address which you can use to complete the enabling process.