Onboarding an Azure account
When adding an Azure subscription, you can choose between two methods of deployment:
ARM deployment
Manual
Select the method you want to use to integrate your account:
Create an Azure AD application from your Azure Portal
Important
If you have already created an Azure AD application from a previous integration, you can skip this section.
Under Scan Configuration, select Add an Azure Subscription.

Under Select a connection method, select the ARM Deployment method.
Open a new browser tab or window and log in to the Azure Portal with an administrator account.
Create an Azure AD application from your Azure Portal:
Navigate to App registrations.
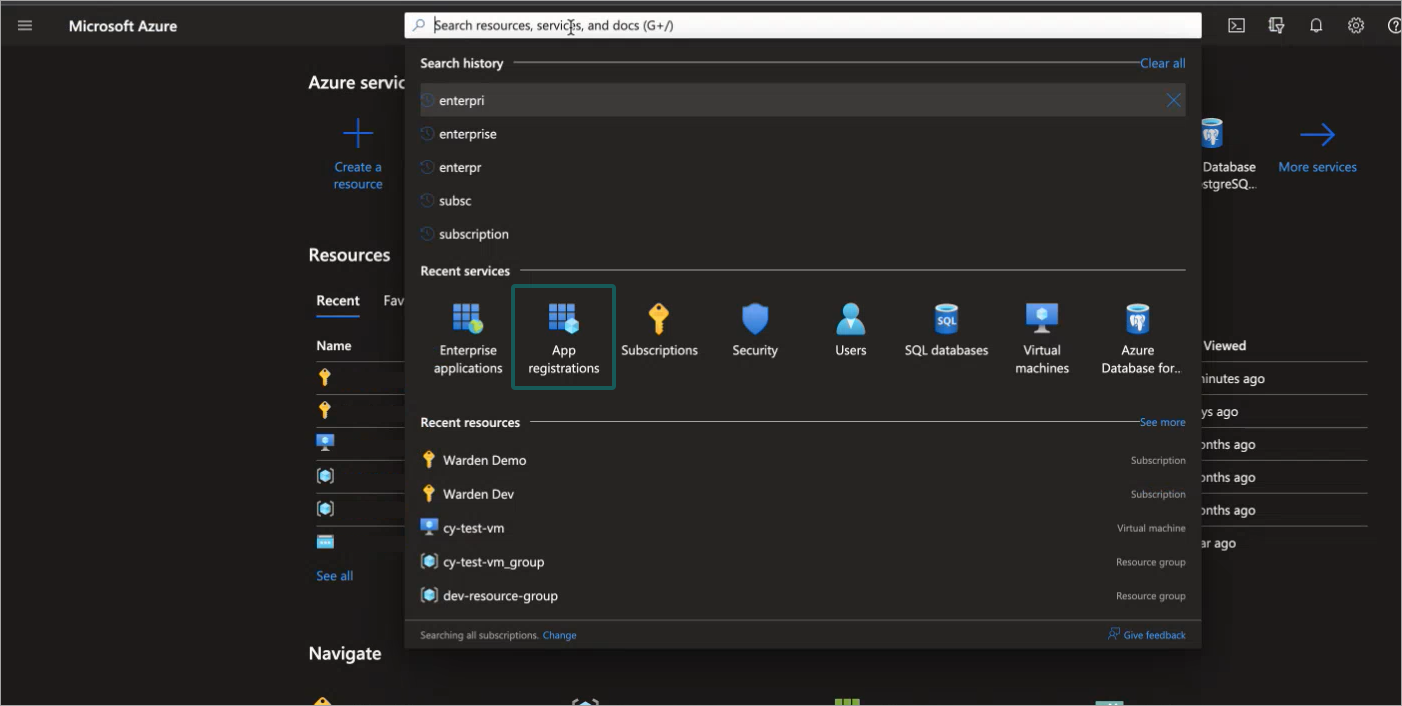
Click New registration.
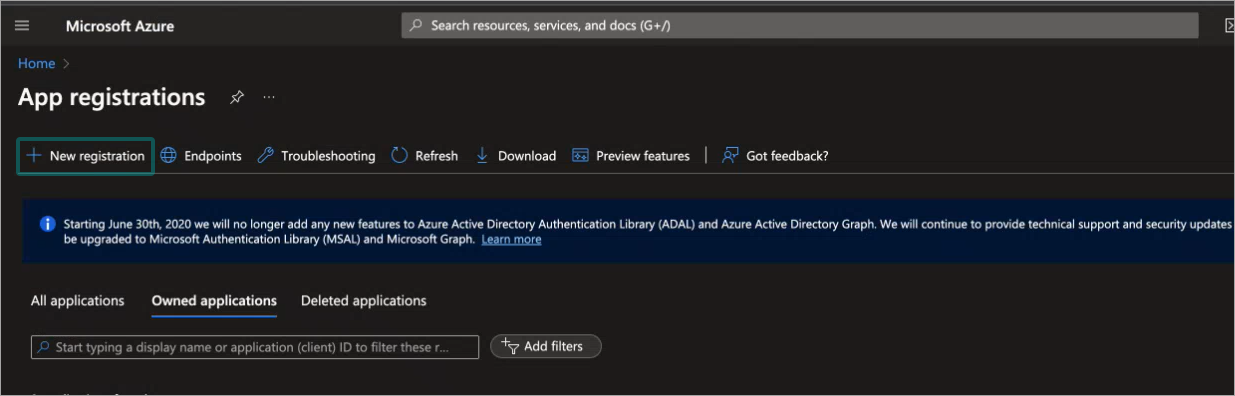
The Register an application window is displayed.
Type in a descriptive name for the application under Name.
Click Register:
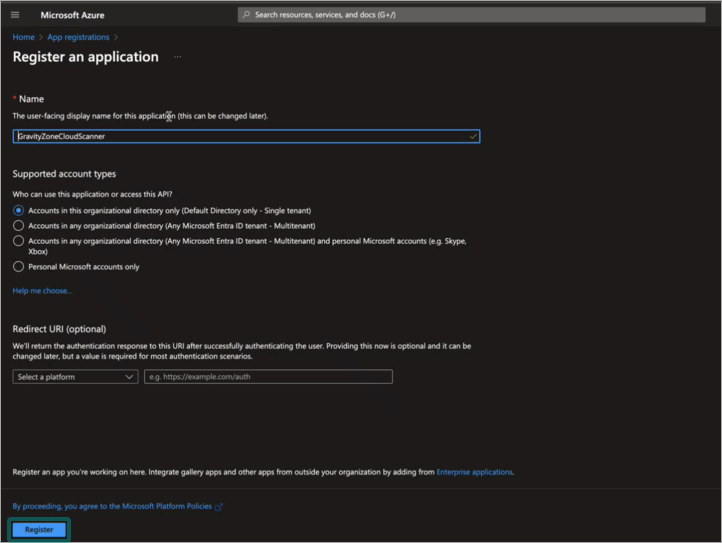
The new application is displayed:
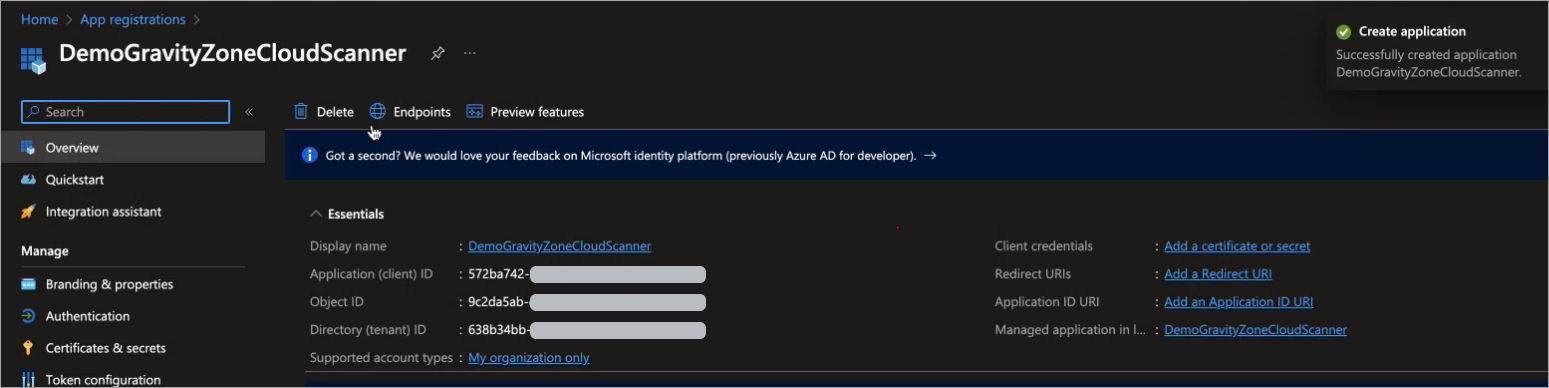
Copy the Application (client) ID and Directory (tenant) ID.
Go back to the Scan Configuration browser page and paste the information copied at step 5.
Add API permissions to the application:
Click the API permissions link in the menu on the left side of the page.
The API permissions page is displayed.
Click + Add permission.
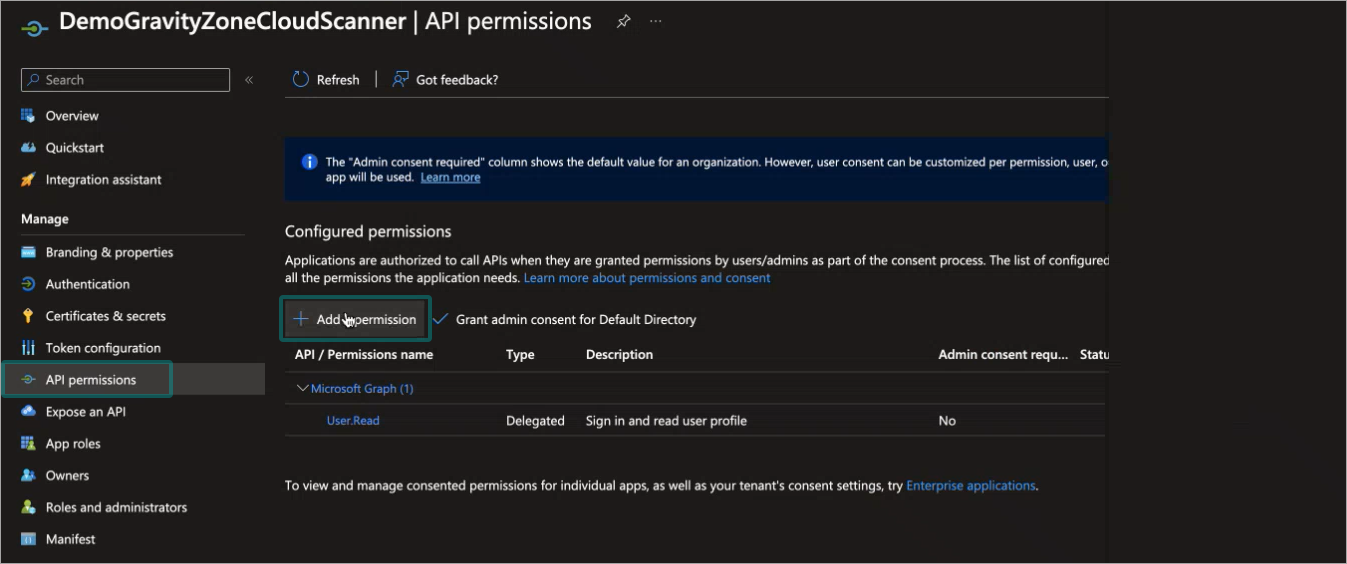
The Request API permissions window is displayed.
Select Microsoft Graph.
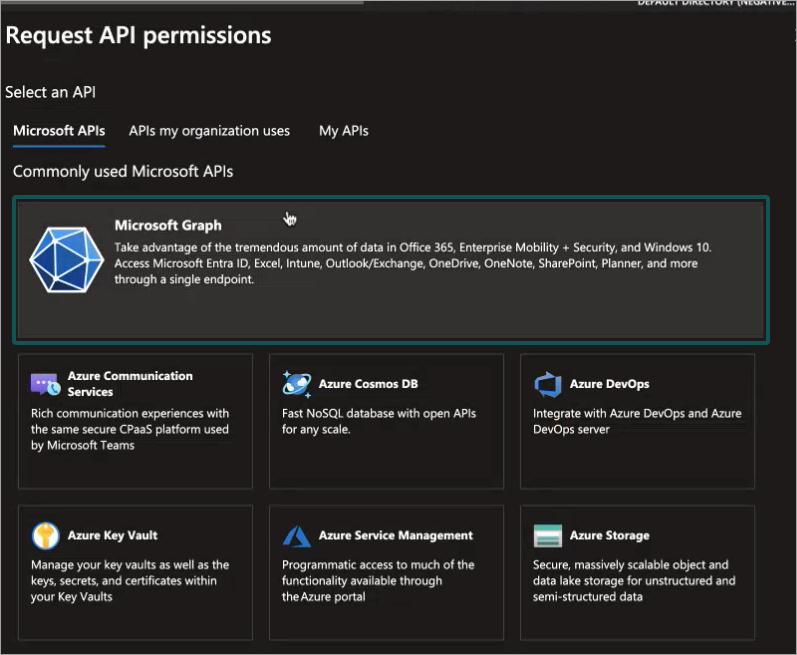
The Microsoft Graph permissions page is displayed.
Click on Application permissions.
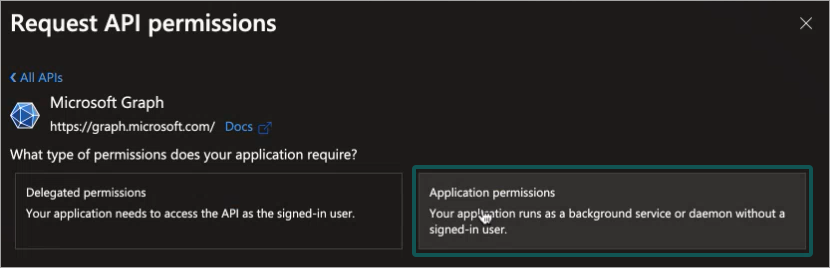
A list of available permissions is displayed.
Add the following permissions:
User.Read.AllGroup.Read.AllApplication.Read.AllUserAuthenticationMethod.Read.All
Click Add permissions.
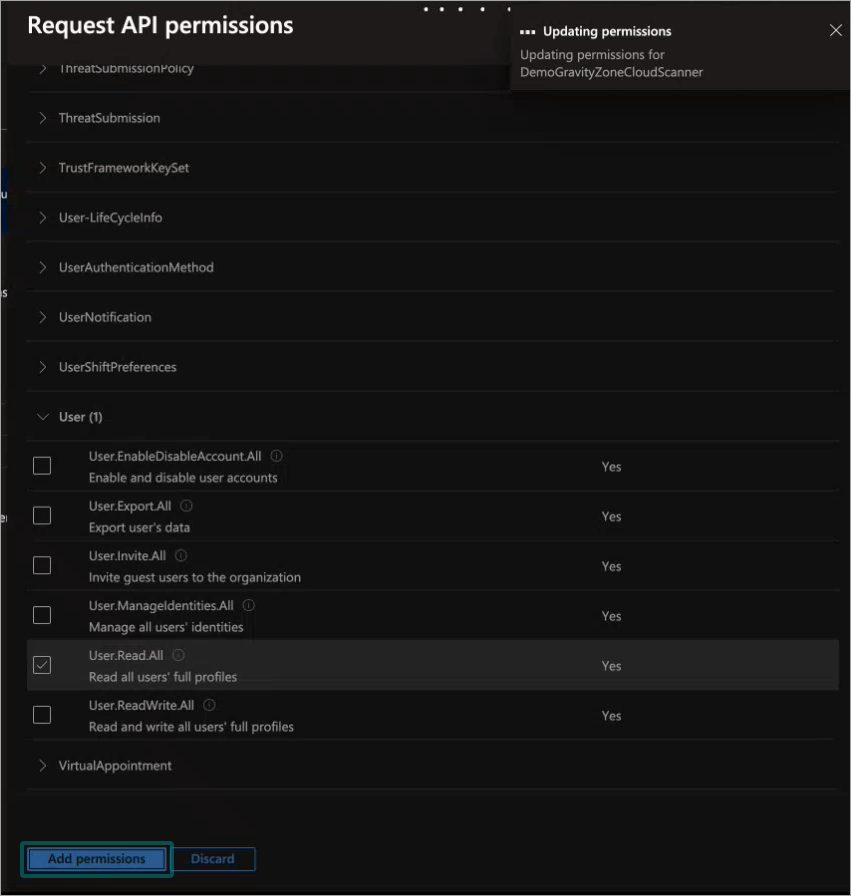
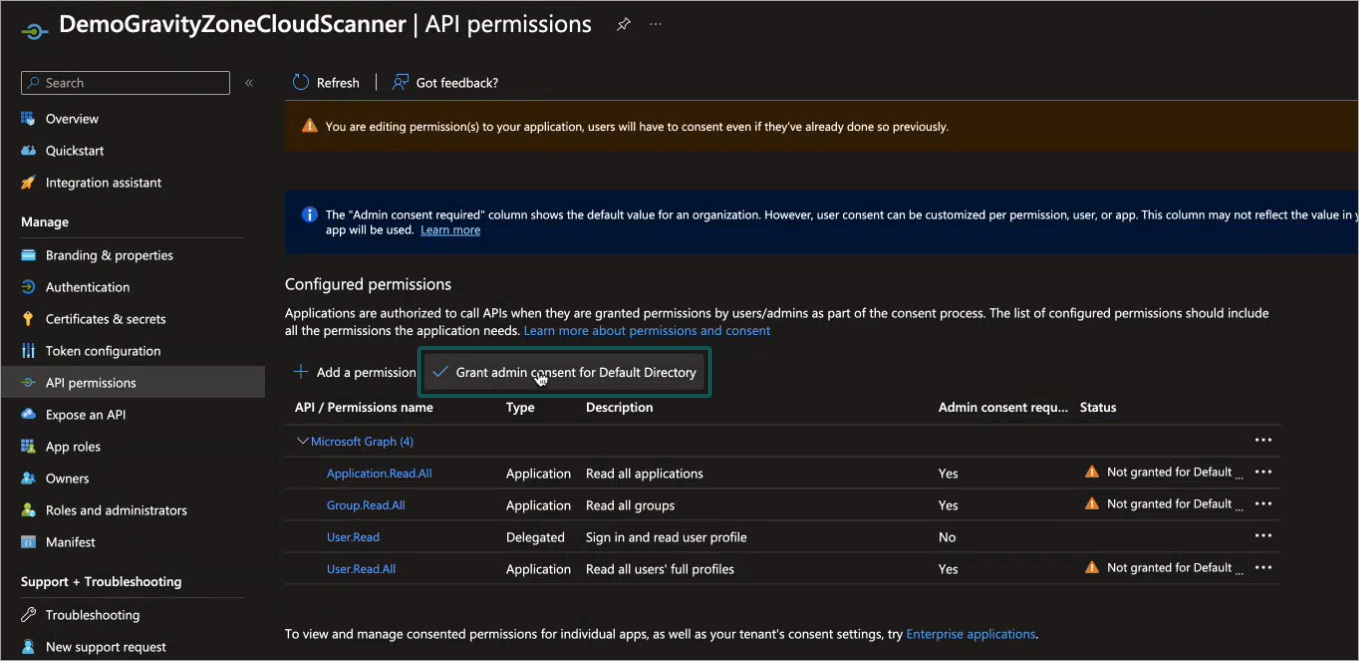
The Configured permissions window is displayed.
Click Grant admin consent for Default Directory.
Set up a Client secret:
Click the Certificates & secrets link in the menu on the left side of the page.
Click + New client secret.
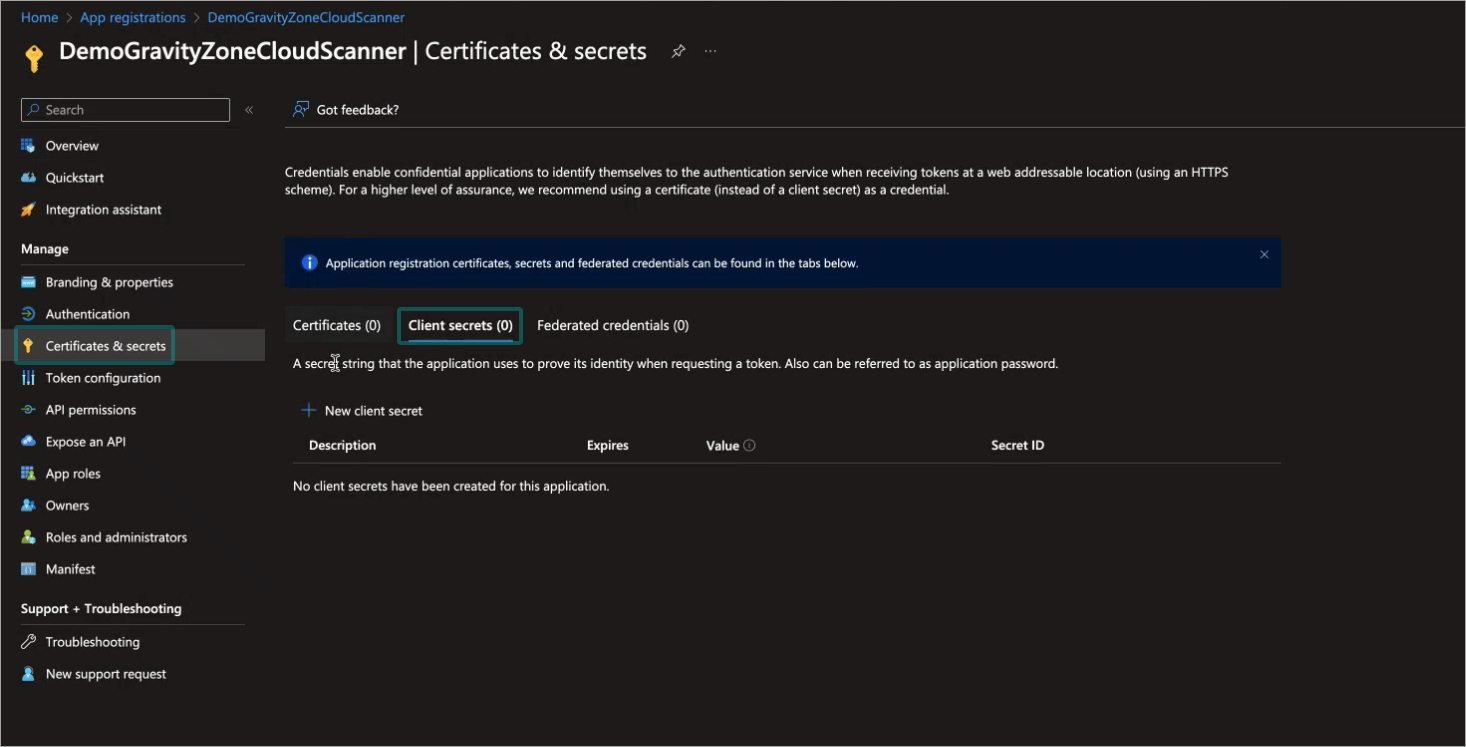
The Add a client secret window is displayed.
Type in an easily identifiable description in the Description field.
Set the Expires setting to 24 months.
Note
When the client secret expires you will have to create a new one and manually add it to the integration.
Click Add.

Important
Do not close or refresh the window until the update is finished.
Copy the value under the Value column of the newly created Client secret.
Go back to the Scan Configuration browser page and paste the information copied at step 9.
Click Add account.
ARM Deployment
Under Select a connection method, select the ARM Deployment method.
Open a new browser tab or window and log in to the Azure Portal with an administrator account.
Go to Azure Active Directory > Enterprise applications.
Search for your application name and click the value under Name column.

The Overview page is displayed.
Copy the values under Application (client) ID and Object ID.
Go back to the Scan Configuration browser page and paste the Application (client) ID information in the field with the same name.
Keep the Object ID for later.
Go to App registrations:

Open the application you want to use and copy the Directory (tenant) ID.
Go back to the Scan Configuration browser page and paste the information in the field with the same name.
Set up a Client secret:
Click the Certificates & secrets link in the menu on the left side of the page.
Click + New client secret.

The Add a client secret window is displayed.
Type in an easily identifiable description in the Description field.
Set the Expires setting to 24 months.
Note
When the secret expires you will have to create a new one and manually add it to the integration.
Click Add.

Important
Do not close or refresh the window until the update is finished.
Copy the value under the Value column of the newly created Client secret.
Go back to the Scan Configuration browser page and paste the information copied at step 9.
Go to the Subscriptions service.

Copy the Subscription ID you want to use.
Go back to the Scan Configuration browser page and paste the information in the field with the same name.
Type in a descriptive name for the account.
Click the Deploy to Azure button.

The Custom deployment page is displayed.
Under Project details, select the Subscription you want to use.
Fill in the information under the Instance details section:
Select the region where your cloud account is located.
Paste the Object ID value copied at step 5 to the Principal Id field.
Type in a descriptive name for the role.
Click Review + create.

Review the displayed information and click Create.
Go back to the Scan Configuration browser page.
Click on the Add account button.

Manual
Under Select a connection method, select the Manual method.
Open a new browser tab or window and log in to the Azure Portal with an administrator account.
Go to Azure Active Directory > Enterprise applications.
Search for your application name and click the value under Name column.

The Overview page is displayed.
Copy the values under Application (client) ID and Object ID.
Go back to the Scan Configuration browser page and paste the Application (client) ID information in the field with the same name.
Keep the Object ID for later.
Go to App registrations:

Open the application you want to use and copy the Directory (tenant) ID.
Go back to the Scan Configuration browser page and paste the information in the field with the same name.
Set up a Client secret:
Click the Certificates & secrets link in the menu on the left side of the page.
Click + New client secret.

The Add a client secret window is displayed.
Type in an easily identifiable description in the Description field.
Set the Expires setting to 24 months.
Note
When the secret expires you will have to create a new one and manually add it to the integration.
Click Add.

Important
Do not close or refresh the window until the update is finished.
Copy the value under the Value column of the newly created Client secret.
Go back to the Scan Configuration browser page and paste the information copied at step 9.
Go to the Subscriptions service.

Copy the Subscription ID you want to use.
Go back to the Scan Configuration browser page and paste the information in the field with the same name.
Click on the link under the Name column for the subscription you want to use.
The Subscription details window is displayed.
Go to the Access control (IAM) page.
Click the + Add button and select Add custom role:

In the Basics tab fill in the following information:
Under Custom role name type in a unique identifier for the role.
In the Description field add in information that will make the role easily identifiable.
Go to the JSON tab.
Go back to the Scan Configuration browser page and access the JSON link.
Copy the
"permissions"parameter.Go back to the JSON tab and paste it over the same parameter.
Click the Save button on the upper right side of section.

Click the Review + create button on the lower left side of the page.
Click the Create button on the lower left side of the page.
The Access control (IAM) page is displayed.
Click the + Add button and select Add role assignment.

The Add role assignment page is displayed.
Click on the name of the role you created earlier.
Note
The role page is displayed.
Click the Next button in the lower side of the page.

The Add role assignment page is displayed.
Under the Members tab, click + Select members.

Select the name of the application for this connection.
Click the Review + assign button on the lower left side of the page.
Go back to the Scan Configuration browser page.
Type in a descriptive name for the account.
Click the Add account button.
