Azure Sentinel
Integrate GravityZone Cloud with Azure Sentinel
To set up the link between Azure Sentinel and GravityZone follow the steps below:
Log in to the Microsoft Azure portal.
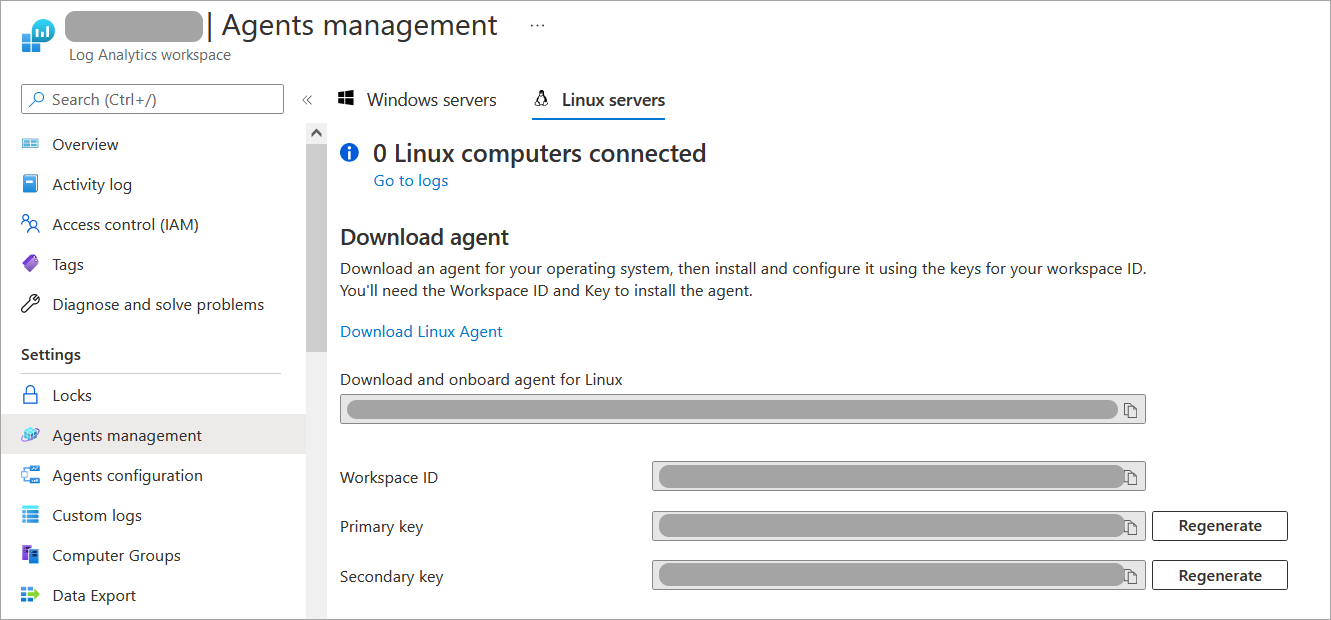
Create a new Log Analytics Workspace in Microsoft Azure Sentinel for receiving GravityZone alerts.
Copy and save the Workspace ID and the Primary key for your newly created workspace.
Note
You can get this information from Microsoft Azure > Log Analytics Workspace > Agents Management > Settings.
Enable Event Push API in GravityZone Control Center:
Log in to GravityZoneControl Center.
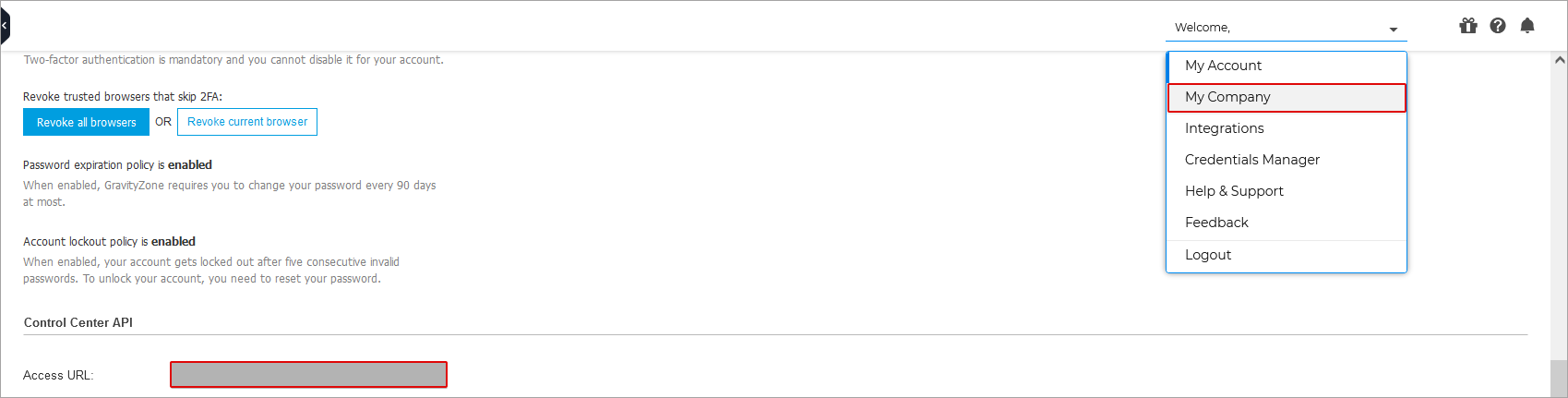
Go to My Account.
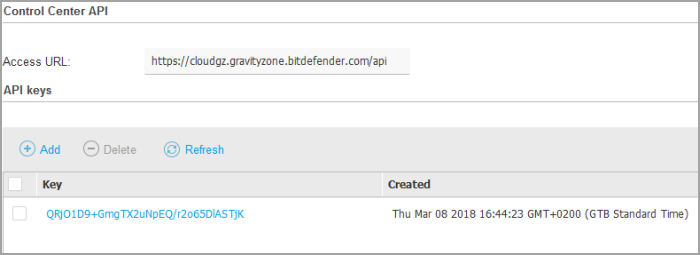
Under API keys section, click Add.
Select the Event Push Service API check box and click Save. The new key appears in the API Keys table.
Click Save to preserve the changes made in My Account page.
Enable the Azure integration manually:
Get the information needed to configure Event Push Service settings from your favorite terminal emulator on Linux or Mac:
GravityZone API URL.
You can find it under MyAccount > Control Center API
The authorization header of the API key generated in GravityZone.
The header value is Basic base64 encode. To obtain the authorization header, run the
echocommand followed by API key with colon (":").> echo –n '604821e87e4c7de3aa15d0e6a97f5ab362281dbf0763746671da2caf4b5cccd1:' | base64 -w 0
The result should be something like this:
NjA0ODIxZTg3ZTRjN2RlM2FhMTVkMGU2YTk3ZjVhYjM2MjI4MWRiZjA3NjM3NDY2NzFkYTJjYWY0YjVjY2NkMTo=
Azure URL.
You can find it here and it should be similar to this format (the settings you have to edit are underlined):
https://CustomerID.ods.opinsights.azure.com/api/logs?api-version=2016-04-01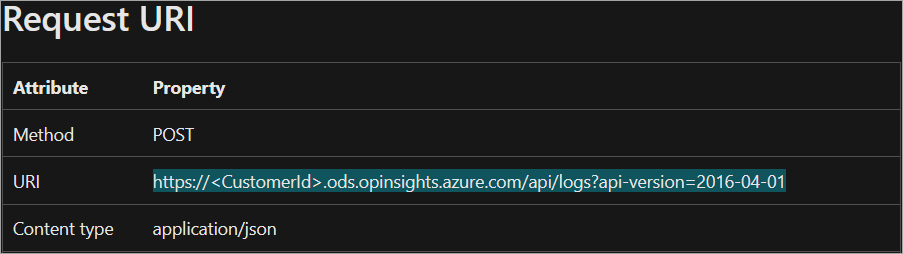
Note
Replace
CustomerIDwith theWorkspaceIDvalue obtained in step 3.HTTP Event Collector token.
The Workspace ID (needed for "workspaceId") and the Primary key (needed for "sharedKey") settings obtained in Step 3.
Run this command (the settings you have to edit are underlined):
curl -k -X POST "https://cloudgz.gravityzone.bitdefender.com/api/v1.0/jsonrpc/push" -H "authorization: Basic NjA0ODIxZTg3ZTRjN2RlM2FhMTVkMGU2YTk3ZjVhYjM2MjI4MWRiZjA3NjM3NDY2NzFkYTJjYWY0YjVjY2NkMTo=" -H "cache-control: no-cache" -H "content-type: application/json" -d '{"params": {"status": 1, "serviceType": "azureSentinel", "serviceSettings": {"workspaceId" : "5e2b52ac-51eb-4cb2-b434-94bb0d39b904", "sharedKey" : "qQgUq1MVDRc8WYYn6zUVOVtaLE/+vmu5G6Ek9qfD2odna+7v5Vb0bF4UxYSHN3MLj6hGjOoigYErjeECXWvkhQ==", "logType" : "GZevent", "requireValidSslCertificate" : false, "url" : "https://5e2b52ac-51eb-4cb2-b434-94bb0d39b904.ods.opinsights.azure.com/api/logs?api-version=2016-04-01"}, "subscribeToEventTypes": {"hwid-change": true,"modules": true,"sva": true,"registration": true,"supa-update-status": true,"av": true,"aph": true,"fw": true,"avc": true,"uc": true,"dp": true,"device-control": true,"sva-load": true,"task-status": true,"exchange-malware": true,"network-sandboxing": true,"malware-outbreak": true,"adcloud": true,"exchange-user-credentials": true,"exchange-organization-info": true,"hd": true,"antiexploit": true}}, "jsonrpc": "2.0", "method":"setPushEventSettings", "id": "1"}'
Note
GravityZone starts sending events to Azure after the Event Push Service settings are reloaded. This happens every 10 minutes.
If you don't want to receive the events from a specific module, remove it from the command. For example, if you don't want to receive events from the exchange module, remove
"exchange-malware": true,from the command.Note
For more information on all associated events refer to this kb article.
The return should be similar to:
{"id":"1","jsonrpc":"2.0","result":true}