Security Telemetry
Important
This feature requires EDR license and it is available only for Windows endpoints.
With Security Telemetry, you have access to underlying data related to security events, so that you can build custom correlations. To ensure optimal performance and data footprint, the agents send only events relevant for the security of your network:
Processes: create, terminate
Files: create, read, modify, move, delete
Registry: create and delete keys, modify and delete value
User access: login
Network connection
There are two available solutions:
Splunk
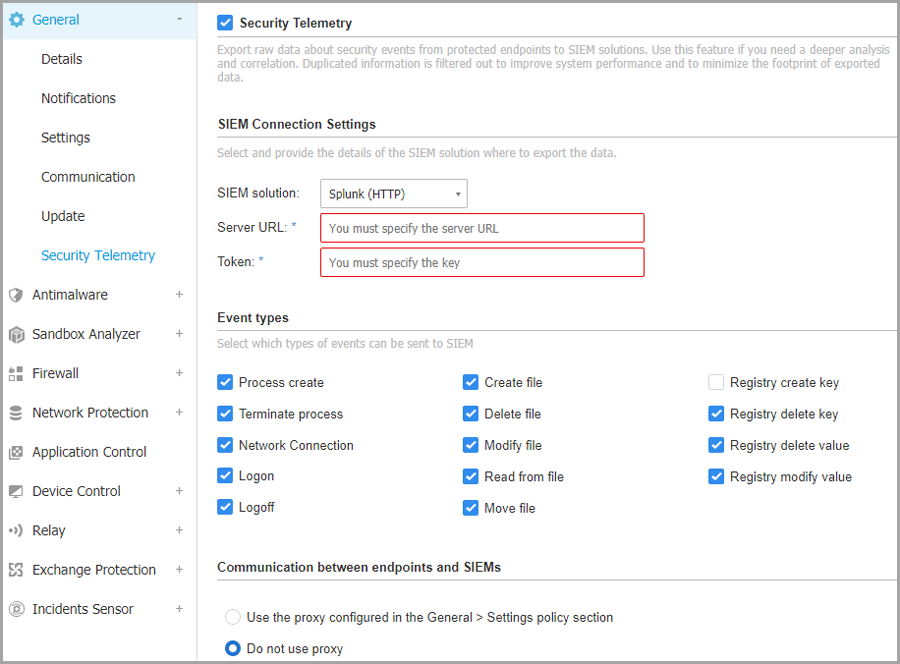
The security agent sends this information in a standard industry format (JSON, CEF), directly to the SIEM solution (Splunk). To view a full list of the events sent to the SIEM solution, refer to Security Telemetry events sent to SIEM.
To send security events from the target endpoints to the SIEM solution, configure the policy as follows:
Select the Security Telemetry check box to enable the feature.
Select the SIEM solution you are going to connect to.
Provide the URL of the SIEM server.
Warning
HTTPS protocol with TLS 1.2 or higher is required, otherwise event submission will fail.
Select Bypass collector CA validation in Control Center, in case a security certificate validation error occurs, but you still want to use the SIEM server against the error.
Such error occurs if GravityZone cannot check the SSL certificate of the HTTP collector against a Certificate Authority or the DNS of the server. For example, when your HTTP collector uses a self-signed security certificate.
Enter the authorization token that secures the connection.
Select the types of events you want to send from the endpoint to the SIEM.
By default, all types of events are sent, except registry key creation.
Under the Communication between endpoints and SIEM, choose whether to use a proxy server.
The agent uses for communication with the SIEM the same proxy server as for the communication with GravityZone.
You can check its settings in the General > Settings section.
Once the policy is applied on endpoints, the agent starts sending events as they occur to the configured SIEM server.
Syslog (JSON)
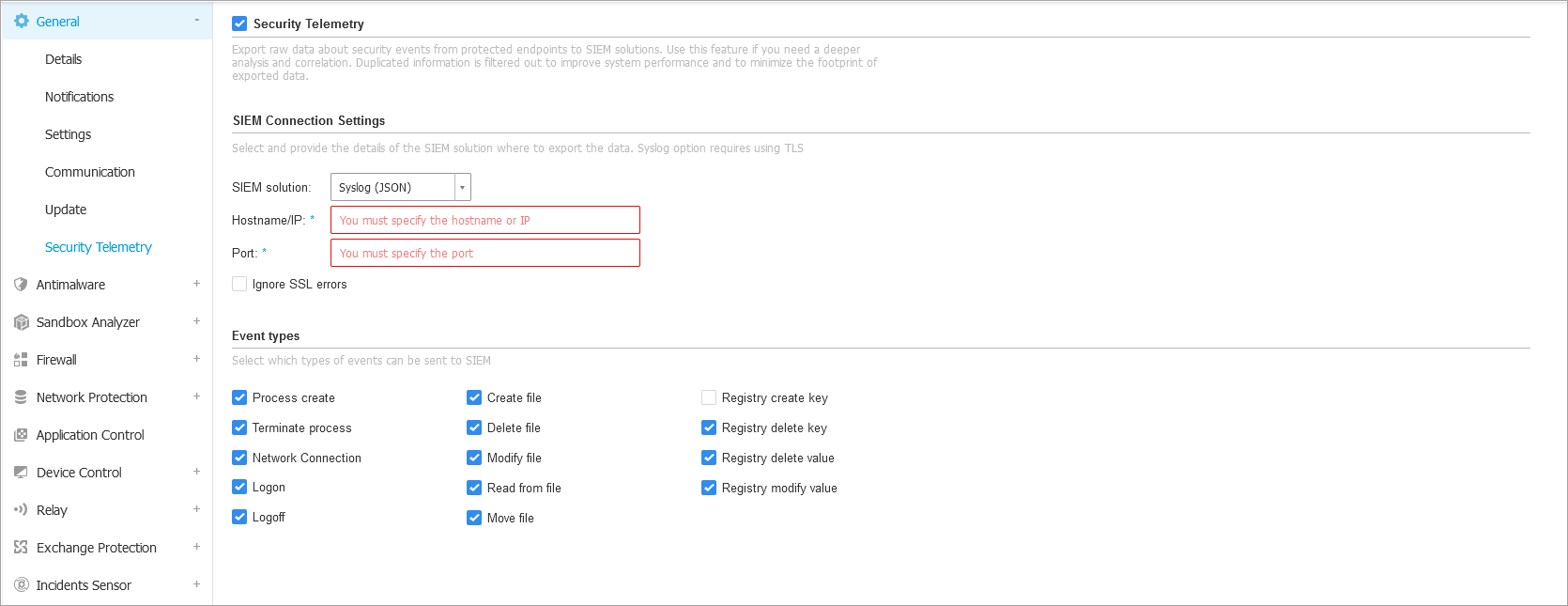
The security agent sends this information in a standard industry format (JSON), directly to the SIEM solution. To view a full list of the events sent to the SIEM solution, refer to Security Telemetry events sent to SIEM.
Note
For messages to be delivered, the target server needs to have Transport Layer Security (TLS) enabled.
To send security events from the target endpoints to the SIEM solution, configure the policy as follows:
Select the Security Telemetry check box to enable the feature.
Under SIEM solution select Syslog (JSON).
Under Hostname/IP type in the hostname or IP of the syslog server.
Enter the port used by endpoints to connect to the syslog server under Port.
Optional: Select Ignore SSL errors if you want to ignore security certificate validation errors. Use this option if you want to use this SIEM server despite any errors that might occur.
Such error occurs if GravityZone cannot check the SSL certificate of the HTTP collector against a Certificate Authority or the DNS of the server. For example, when your HTTP collector uses a self-signed security certificate.
Select the types of events you want to send from the endpoint to the SIEM.
By default, all types of events are sent, except registry key creation.