Addressing Google Drive issues with Bitdefender Endpoint Security Tools on Windows and macOS
The interaction between Bitdefender Endpoint Security Tools (BEST) and Google Drive may result in performance issues on endpoints during scheduled scans. To avoid these issues, you need to add exclusions or make certain configurations in the GravityZone Control Center.
This article discusses several scenarios and the possible solutions on Windows and macOS endpoints.
BEST for Windows and Google Drive
On Windows, you may encounter the following scenarios while using Google Drive:
Scenario 1- BEST scans the Google drive every time a full scan runs on endpoint
Issue
Bitdefender Endpoint Security Tools (BEST) scans the same files, multiple times, over the internet. This action results in downloading files offline and consuming disk space.
Solution
To exclude the Google (G:) drive from scanning, you must add a folder exclusion with the following details:
Path:
G:\Modules: On-demand
The On-access module still provides full protection for that location.
When adding the exclusion, pay attention to Google virtual drive naming behavior:
If the drive letter
G:is available, Google Drive uses it to map the virtual drive.If
G:is not available (already in use), Google Drive uses the first available drive letter.
If Google Drive uses a different drive letter, make sure you also add that letter as an exclusion.
To learn how Google Drive assign mount letters to the virtual drive, refer to this article from Google.
Scenario 2 - BEST scans the local Google Drive cache
This action makes the files keep resyncing or getting downloaded offline and it's taking space on the endpoint.
Create folder and process exclusions as follows:
Folder exclusion
Path:
%LOCALAPPDATA%\Google\DriveFSModules: On-demand, On-access, ATC/IDS
Process exclusion
The path from your system configuration for
GoogleDriveFS.exeModules: On-access, ATC/IDS
Scenario 3 - BEST scans the Google Drive drive every time the application is started and the drive is mounted
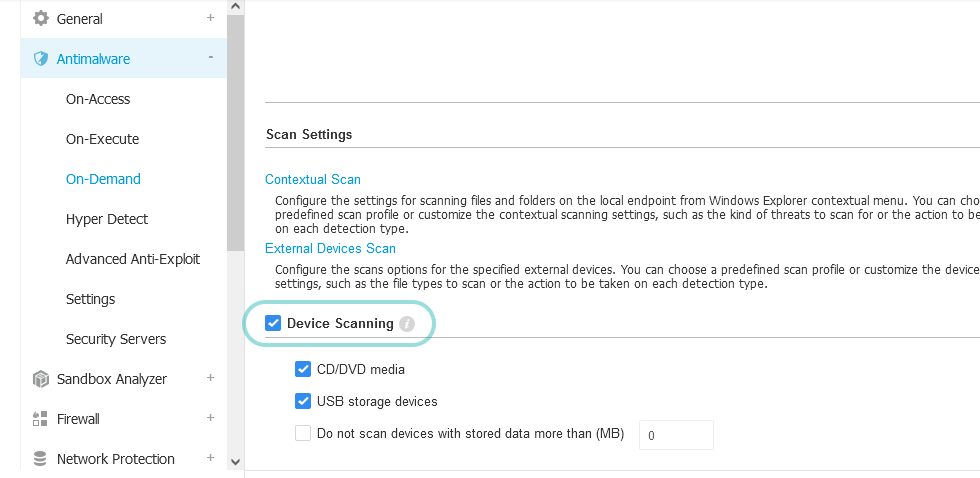
This action causes resource consumption and it happens because the Device Scanning option is active in the policy (for details, refer to Antimalware On-Demand).
This issue can be fixed by one of the following solutions:
Disable the Device Scanning option in the policy. As long as On-access scanning is functional on the endpoint, this action does not affect security.
Disable USB storage devices scan in Device Scanning. As long as On-access scanning is functional on the endpoint, this action does not affect security.
Set a size limit for the Do not scan devices with stored data more than (MB) option (for example: 100 MB).
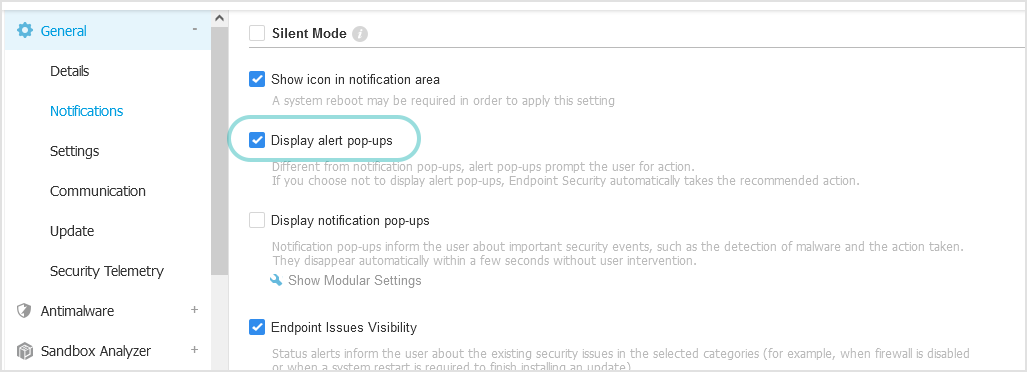
Enable the Display alert pop-ups option in the General > Notifications settings of the policy. This action allows you to choose whether to scan the attached drive or not.
Scenario 4 - I want to block Google Drive when using the Device Control module
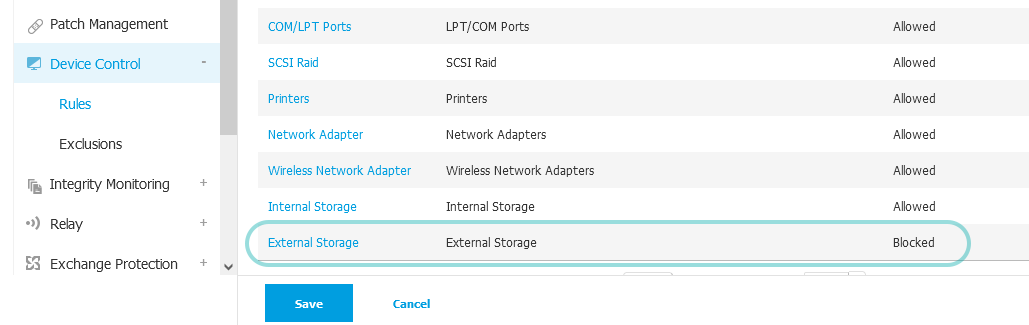
Google Drive causes resource consumption when having the Device Control module active on endpoint. This happens because GravityZone matches the Google virtual drive to the External Storage > Other category.
To block Google Drive, you can choose one of these options:
Block the entire External Storage category. To do this, open the External Storage category and, for Permission select Blocked.
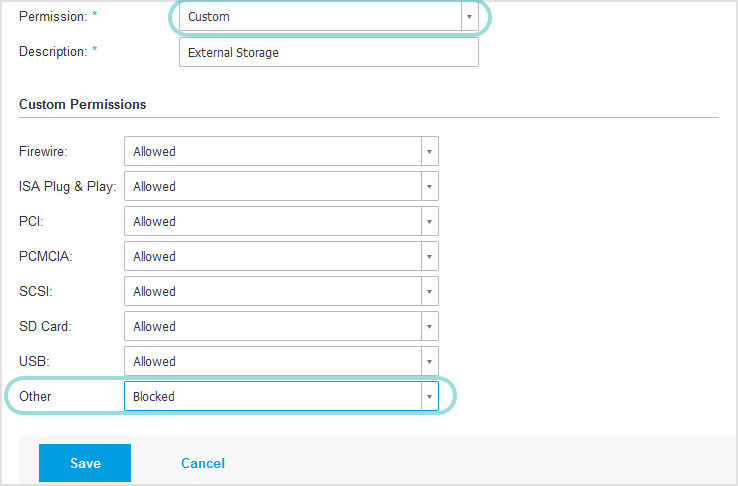
Block only the Other category in External Storage. Follow these steps:
Open the External Storage category.
For Permission, select Custom.
Under Customer Permissions, go to Other and select Blocked.
Bitdefender Endpoint Security Tools for Mac and Google Drive
On macOS, Bitdefender Endpoint Security Tools (BEST) is constantly scanning the local Google Drive cache and mount point.
This behavior makes the files keep resyncing or getting downloaded offline, which takes space on the endpoint. In addition, the endpoint may experience high CPU usage due to constant scanning activity.
To avoid these issues, configure folder and process exclusions as follows:
Folder exclusions
Path:
/Volumes/GoogleDrive/Modules: On-demand, On-Access, ATC/IDS
Path:
~/Library/Application Support/Google/DriveFS/Modules: On-demand, On-Access, ATC/IDS
Process exclusion
Path:
/Applications/Google Drive File Stream.app/Contents/MacOS/Google Drive File StreamModules: On-Access, ATC/IDS
The On-access scanning module will still offer full protection for the location.
Using exclusions in GravityZone
To add exclusions in GravityZone Control Center, go to the Policies page, open a policy and use the options in the Antimalware > Settings section. You can configure in-policy exclusions (only applicable to that policy) or assign an exclusion list from configuration profiles (applicable to multiple policies).
For details on how exclusions work in policies, refer to Exclusions.
For details on adding exclusions in configuration profiles, refer to Configuration profiles.
For details on process exclusions for macOS, refer to Adding process exclusions for Mac in GravityZone.