Update
Updates are very important as they allow countering the latest threats. Bitdefender publishes all product and security content updates through the Bitdefender servers on the Internet. All updates are encrypted and digitally signed so that they cannot be tampered with.
Update process flow
When a new update is available, the Bitdefender security agent checks the digital signature of the update for authenticity, and the contents of the package for integrity.
Next, each update file is parsed and its version is checked against the installed one.
Newer files are downloaded locally and checked against their MD5 hash to make sure they are not altered.
In this section, you can configure the Bitdefender security agent and security content update settings.
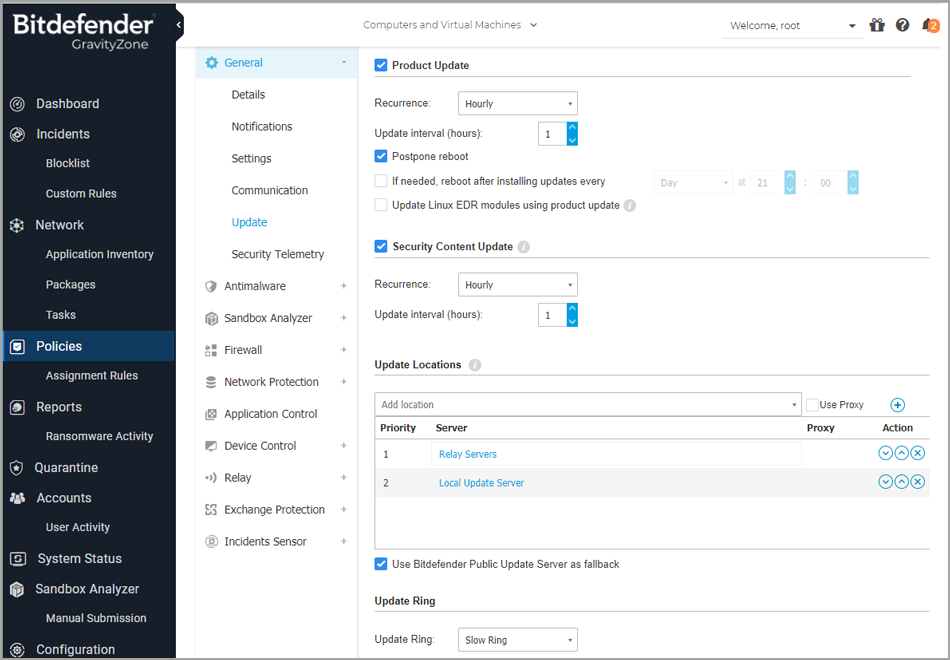
Product Update
Bitdefender security agent automatically checks for, downloads and installs updates every hour (default setting).
Automatic updates are performed silently in the background.
Recurrence - To change the automatic update recurrence, choose a different option from the menu and configure it according to your needs in the subsequent fields.
Postpone reboot - Some updates require a system restart to install and work properly. By default, the product will keep working with the old files until the computer is restarted, after which it will apply the latest updates.
A notification in the user interface will prompt the user to restart the system whenever an update requires it.
It is recommended to leave this option enabled, otherwise, the system will automatically reboot after installing an update that requires it.
Users will be notified to save their work, but the reboot cannot be canceled.
If you choose to postpone reboot, you can set a convenient time when computers will reboot automatically if (still) needed. This can be very useful for servers.
Select If needed, reboot after installing updates and specify when it is convenient to reboot (daily or weekly on a certain day, at a certain time of day).
For more control over when changing the configuration and updating the staging process, you can configure the BEST agent on your Linux machines to execute EDR kernel module updates via Product Update.
When the Product Update check box enabled:
If you enable the Update Linux EDR modules using product update check box, GravityZone will update kernel versions via Product Update.
If you leave this option disabled, the kernel versions will be updated via Security Content Update.
If you enable the Update Linux EDR modules using product update check box but disable the Product Update option, the Linux EDR modules will not be updated.
Security Content Update
Security content refers to static and dynamic means of detecting threats, such as, but not limited to, scan engines, machine learning models, heuristics, rules, signatures, and blacklists.
Bitdefender security agent automatically checks for security content update every hour (default setting). Automatic updates are performed silently in the background.
To change the automatic update recurrence, choose a different option from the menu and configure it according to your needs in the subsequent fields.
Note
Security content updates are automatically performed with each product update to ensure optimal performance.
Update Locations
Bitdefender security agent’s default update location is the local GravityZone update server.
Note
Add an update location either by choosing the predefined locations from the drop-down menu or by entering the IP or hostname of one or several update servers in your network.
Configure their priority using the up and down buttons displayed on mouse-over. If the first update location is unavailable, the next one is used.
To set a local update address, enter the address of the update server in the Add location field.
You can:
Choose a predefined location:
Relay Servers - The endpoint will automatically connect to its assigned Relay Server. You can check the assigned Relay Server in the Information window. For more details refer to Viewing Computer Details.
Warning
Relay Servers are not supported on legacy operating systems.
Local Update Server - Enter the IP or hostname of one or several update servers in your network.
Use one of these syntaxes:
update_server_ip:portupdate_server_name:port
The default port is 7074.
The Use Bitdefender Servers as fallback location check box is selected by default. If the update locations are unavailable, the fallback location will be used.
Warning
Disabling the fallback location will stop automatic updates, leaving your network vulnerable when the provided locations are unavailable.
If client computers connect to the local update server through a proxy server, select Use Proxy.
Click the
 Add button.
Add button.Use the
 Up /
Up /  arrows in the Action column to set priority of defined update locations. If the first update location is not available, the next one is taken into account.
arrows in the Action column to set priority of defined update locations. If the first update location is not available, the next one is taken into account.To remove a location from the list, click the corresponding
 Delete button. Although you can remove the default update location, this is not recommended.
Delete button. Although you can remove the default update location, this is not recommended.
Update Ring
You can roll out product updates in phases, using update rings:
Fast Ring. The machines with a fast ring policy will receive the newest available updates. This setting is recommended for the non-critical machines in production.
Slow Ring. The endpoints with a Slow ring policy will receive updates at a later date, depending on the response received from the Fast ring endpoints. It is a precautionary measure in the update process. This is the default setting.
Important
In the unlikely event that an issue occurs on the fast ring on machines with a particular configuration, it will be fixed before the Slow ring update.
BEST for Windows Legacy does not support staging. The legacy endpoints on staging location must be moved to the production location.
Note
For details on how the update rings selection affects staging, refer to Update GravityZone.