Content Control
The Content Control settings are organized into the following sections:
Note
The Content Control module is available for:
Windows for workstations
Windows for servers
macOS
Important
On macOS endpoints, Content Control relies on a system extension. Installing the Bitdefender extension requires your approval on macOS High Sierra (10.13) and later. The system notifies the user that a system extension from Bitdefender was blocked. You can allow it from Security & Privacy preferences. Until the user approves the Bitdefender system extension, this module will not work and the Bitdefender Endpoint Security Tools user interface will show a critical issue prompting for approval.
To eliminate user intervention, you can pre-approve the Bitdefender extension by whitelisting it using a Mobile Device Management tool. For details about Bitdefender extensions, refer to Bitdefender system extension blocked in macOS .
Web Access Control
Web Access Control enables you to allow or block web access for users or applications during specified time intervals.
The web pages blocked by Web Access Control are not displayed in the browser. Instead, a default web page is displayed informing the user that the requested web page has been blocked by Web Access Control.
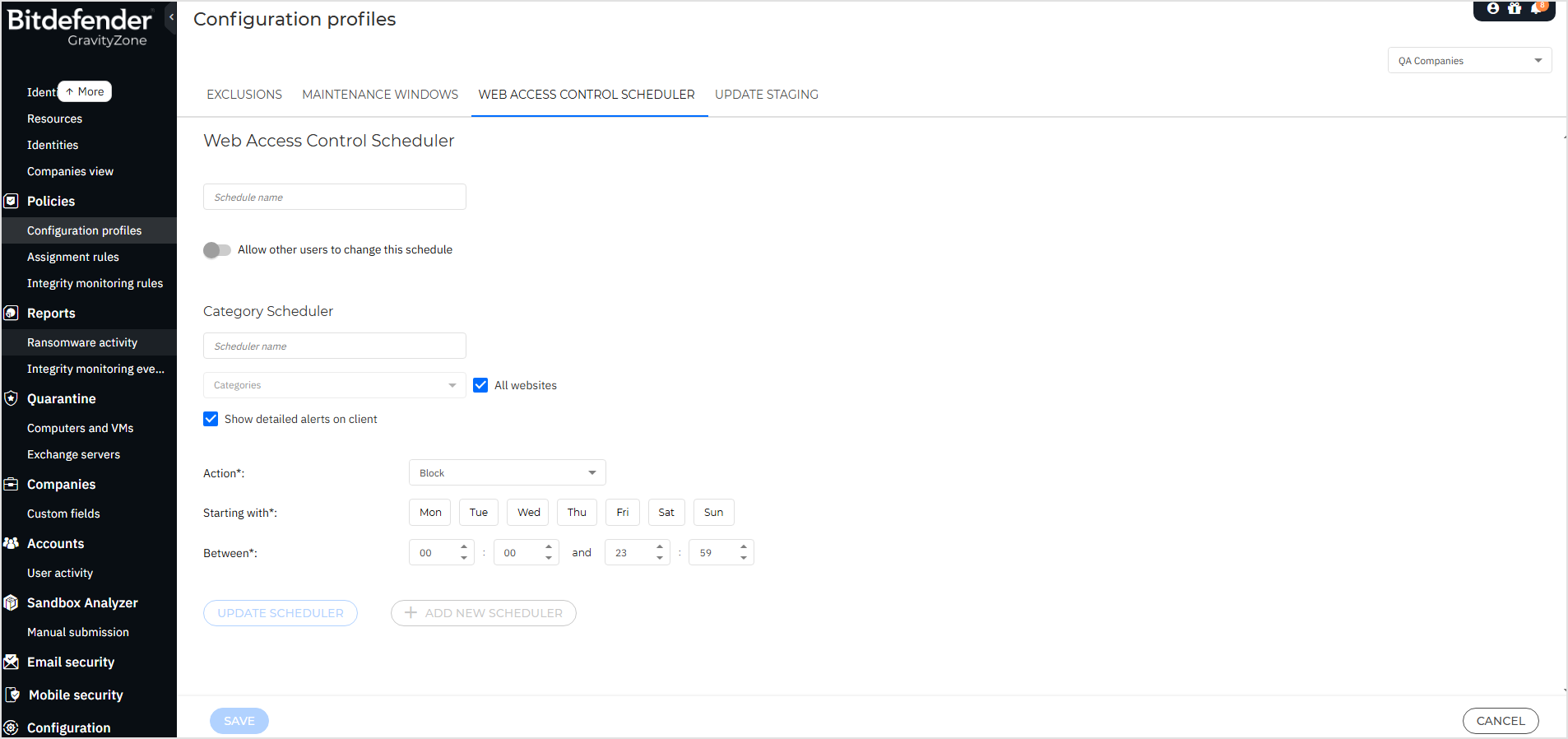
To start using the Web Access Control feature you first must create a schedule, by following the bellow procedure:
Log in to GravityZoneControl Center.
In Configuration profiles go to Web Access Control Scheduler.
Access Add Schedule.
Add the Schedule Name.
Use the toggle to allow other users to edit the schedule.
In the Scheduler field add a new Category Scheduler and set it up.
Note
Make sure the start time occurs before the end time.
In the Categories section choose the categories.
In the Action section choose the action you want taken.
Select the timeframe for the selected action from the Starting with and Between,
Add the new schedulers to the schedule by using the Add new scheduler button.
Save the schedule.
Note
Existing users of GravityZone before version 6.35.1-1 have their Web Access Control settings automatically migrated from their previous location in Network Protection to the new dedicated section in Configuration Profiles.
To assign a schedule to a policy follow the steps bellow:
Go to Policies and click Add to create a new policy, or open an existing one to edit it.
In the Content Control section access Web Access Control .
Use the switch to turn Web Access Control on or off.
From the Assign Schedule drop-down select the schedule you want to apply.

Click Save.
Note
The scheduling sequence is essential since the first match rule will determine whether or not a web page is permitted. The rules will be executed sequentially. Access to web pages will be determined by the action specified in the first match.
You can further configure your settings and exceptions by accessing the Settings section and setting up the Time limiter and Exclusions as follows:
Time limiter
To restrict the Internet access to certain times of the day on a weekly basis:
Use the switch to turn Web Access Control on or off.
You have three configuration options:
Select Allow to always grant web access.
Select Block to always deny web access.
Select Schedule to enable time restrictions on web access based on a detailed schedule.
Note
Bitdefender security agent will perform updates every hour, no matter if web access is blocked.
Select from the grid the time intervals during which you want Internet access to be blocked. You can click individual cells, or you can click and drag to cover longer periods. Click again in the cell to reverse the selection.
To start a new selection, click Allow all or Block all, depending on the type of restriction you wish to implement.
Click Save.
Exclusions
You can also define web rules to explicitly block or allow certain web addresses, overriding the existing Web Access Control settings. Users will be able, for example, to access a specific webpage also when the web browsing is blocked by Web Access Control.
To create a web rule:
Enable the Use Exceptions option.
Enter the address you want to allow or block in the Web Address field.
Select Allow or Block from the Permission menu.
Click the
 Add button at the right side of the table to add the address to the exceptions list.
Add button at the right side of the table to add the address to the exceptions list.Click Save.
To edit a web rule:
Click the web address you want to edit.
Modify the existing URL.
Click Save.
To remove a web rule, click the corresponding
 Delete button.
Delete button.
Application Blacklisting
In this section you can configure Application Blacklisting, which helps you completely block or restrict users' access to applications on their computers. Games, media and messaging software, as well as other categories of software and malware can be blocked in this way.

To configure Application Blacklisting:
Enable the Application Blacklisting option.
Specify the applications you want to restrict access to. To restrict access to an application:
Click the
 Add button at the upper side of the table. A configuration window is displayed.
Add button at the upper side of the table. A configuration window is displayed.You must specify the path to the application executable file on the target computers. There are two ways to do this:
Choose from the menu a predefined location and complete the path as needed in the edit field. For example, for an application installed in the
Program Filesfolder, select%ProgramFilesand complete the path by adding a backslash (\) and the name of the application folder.Enter the full path in the edit field. It is advisable to use system variables (where appropriate) to make sure the path is valid on all target computers.
Access Scheduler. Schedule the applications access during certain times of day on a weekly basis:
Select from the grid the time intervals during which you want to block access to the application. You can click individual cells, or you can click and drag to cover longer periods. Click again in the cell to reverse the selection.
To start a new selection, click Allow All or Block All, depending on the type of restriction you wish to implement.
Click Save. The new rule will be added to the list.
To remove a rule from the list, select it and click the  Delete button at the upper side of the table. To edit an existing rule, click it to open its configuration window.
Delete button at the upper side of the table. To edit an existing rule, click it to open its configuration window.
Data Protection
Data Protection prevents unauthorized disclosure of sensitive data based on administrator-defined rules.
Note
This feature is not available for macOS.

You can create rules to protect any piece of personal or confidential information, such as:
Customer personal information
Names and key details of in-development products and technologies
Contact information of company executives
Protected information might include names, phone numbers, credit card and bank account information, email addresses and so on.
Based on the data protection rules you create, Bitdefender Endpoint Security Tools scans the web and outgoing email traffic for specific character strings (for example, a credit card number). If there is a match, the respective web page or email message is blocked in order to prevent protected data from being sent.
The functionality of Content Control exclusions is not applicable to internal traffic, therefore, the exclusion based on IP and hostname will not be effective.
The user is immediately informed about the action taken by Bitdefender Endpoint Security Tools through an alert web page or email.
To configure Data Protection:
Use the checkbox to turn on Data Protection.
Create data protection rules for all of the sensitive data you want to protect.
To create a rule:
Click the
 Add button at the upper side of the table.
Add button at the upper side of the table.A configuration window is displayed.
Enter the name under which the rule will be listed in the rules table.
Choose a suggestive name so that you or other administrator can easily identify what the rule is about.
Select the type of data you want to protect.
Enter the data you want to protect (for example, the phone number of a company executive or the internal name of a new product the company is working on).
Any combination of words, numbers or strings consisting of alphanumerical and special characters (such as @, # or $) is accepted.
Make sure to enter at least five characters in order to avoid the mistaken blocking of email messages and web pages.
Important
Provided data is stored in encrypted form on protected endpoints, but it can be seen on your Control Center account.
For extra safety, do not enter all of the data you want to protect.
In this case, you must clear the Match whole words option.
Configure the traffic scan options as needed.
Scan web (HTTP) traffic - scans the HTTP (web) traffic and blocks the outgoing data that matches the rule data.
Note
If Intercept Encrypted Traffic is enabled, HTTPS traffic will be scanned as well.
Scan email (SMTP traffic) - scans the SMTP (mail) traffic and blocks the outgoing email messages that contain the rule data.
You can choose to apply the rule only if the rule data matches whole words or if the rule data and the detected string case match.
Click Save.
The new rule will be added to the list.
Configure exclusions to data protection rules so that users can still send protected data to authorized websites and recipients.
Exclusions can be applied globally (to all rules) or to specific rules only.
To add an exclusion:
Click the
 Add button at the upper side of the table.
Add button at the upper side of the table.A configuration window is displayed.
Enter the web or email address that users are authorized to disclose protected data to.
Select the type of exclusion (web or email address).
From the Rules table, select the data protection rules(s) on which this exclusion should be applied.
Click Save. The new exclusion rule will be added to the list.
Note
If an email containing blocked data is addressed to multiple recipients, those for which exclusions have been defined will receive it.
To remove a rule or an exclusion from the list, click the corresponding  Delete button at the right side of the table.
Delete button at the right side of the table.